Published: Nov 13, 2025 by Isaac Johnson
In the last week I’ve looked in detail at UpCloud which is an amazing Finish Cloud Company. But there are some that are more than are based in Europe we’ve yet to explore.
Today I’ll look at OVHCloud and Hetzner. OVHCloud is French provider that has been around since 1999 and headquartered in Roubaix, FR. Hetzner Online GmbH is based out of Gunzenausen, Bavaria in Germany and was founded in 1997. Basically, these are both very solid long-standing companies.
Let’s start with OVHCloud…
OVHcloud
I can easily signup from the login page
NOTE: I did this without any referral so I just have to pay retail for stuff.. here is some other person’s referral code - not even sure whom - but at least you get $10 or $20 in credits.. sadly i didn’t do this…
I just need to give some basic details
We can pick our account type. I’ll use “Private individual”
They have new portal in beta which I’ll use. I need to create a project
I’ll give it a name
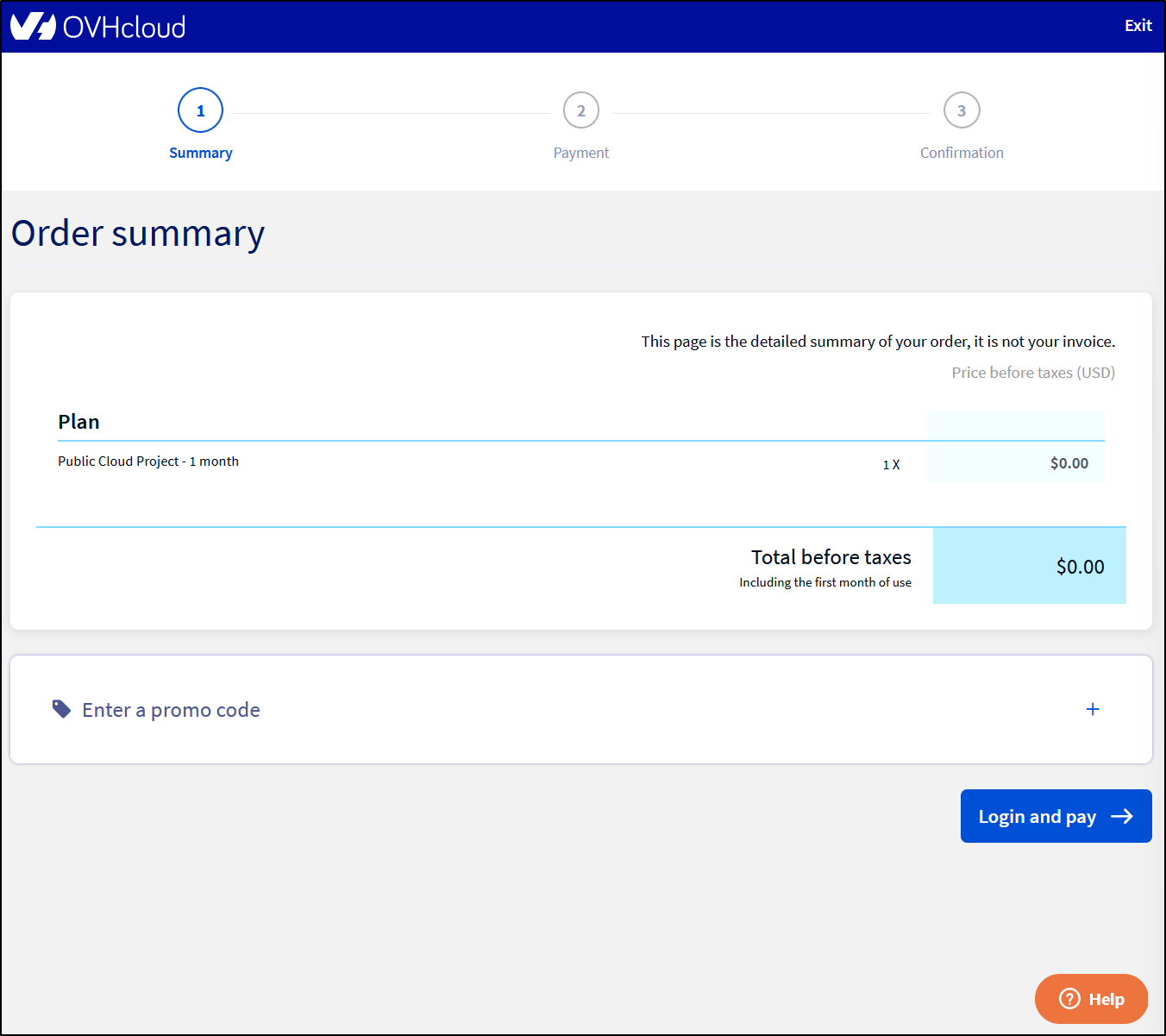
It then sent me to a billing page to pay US$0. A little confusing as to why…
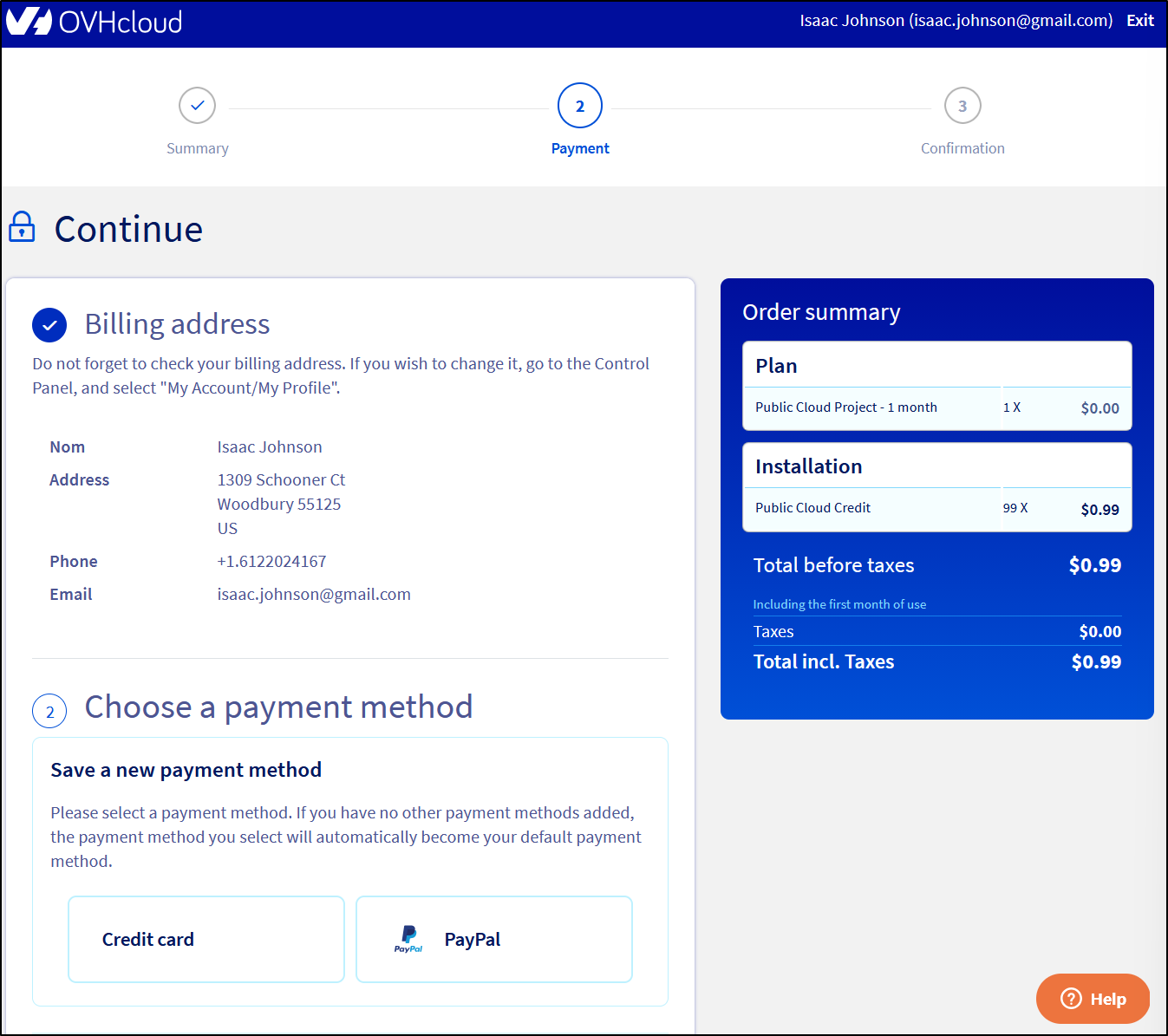
Ah, they charge me a $1 just so we can get a payment method setup.
I then saw the order was processed
Now when I go back to the Project picker, I can pick my “freshbrewedtest” project
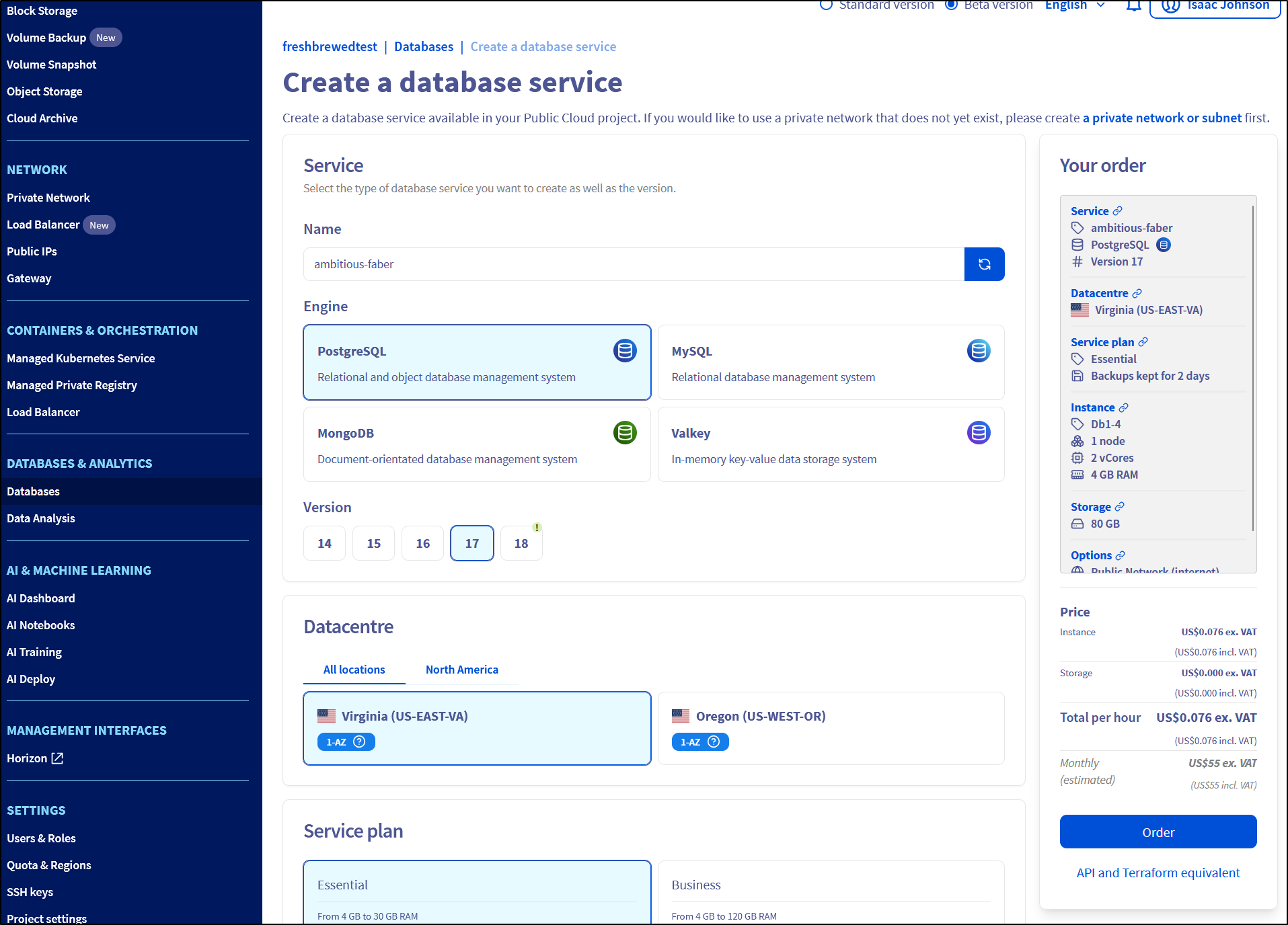
Databases
They have PostgreSQL, MySQL, MongoDB and Valkey available (I don’t consider memorystores databases, but we can save that argument for another time)
The cheapest is US$55.50 a month
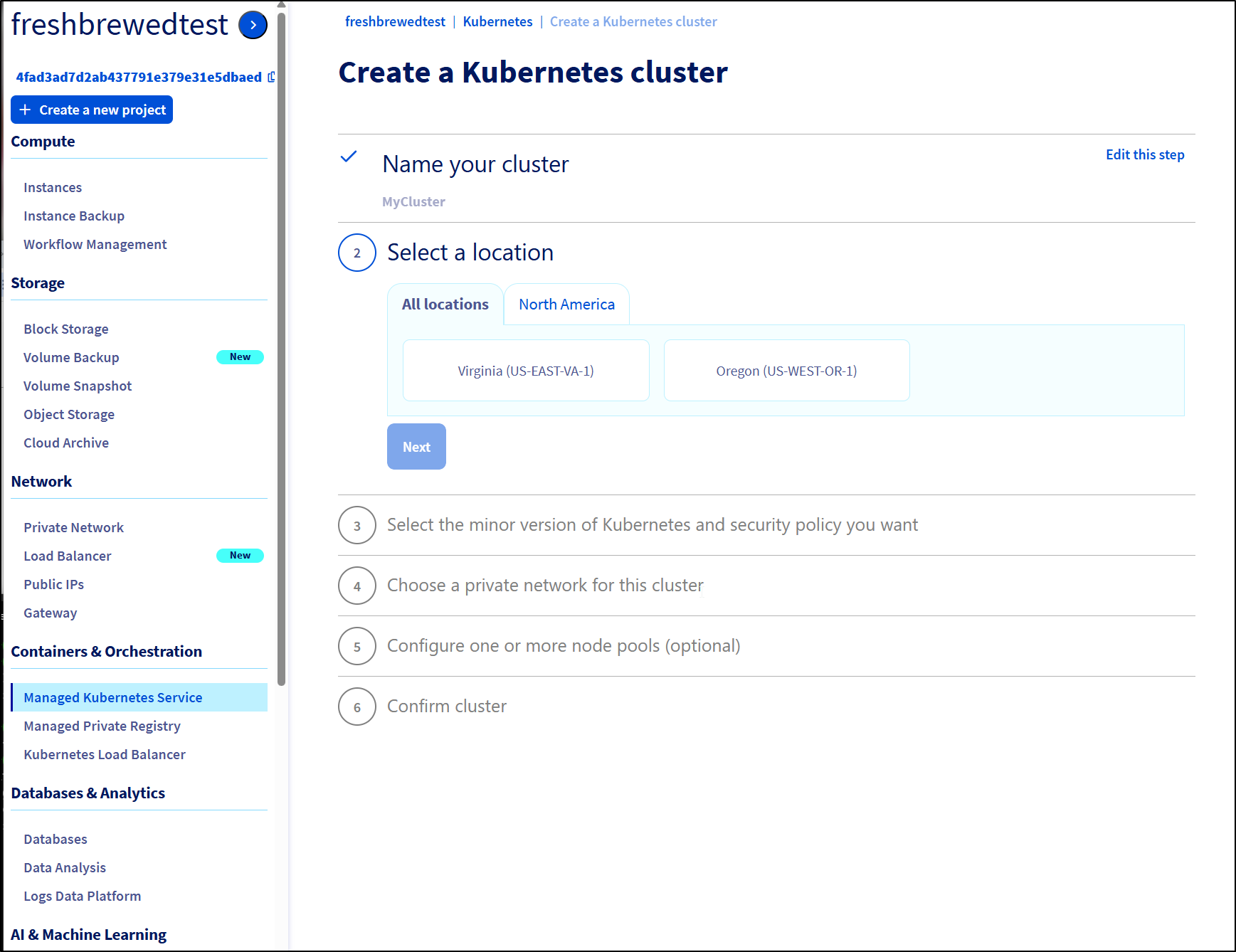
My challenge here is I’m trying to not be in the US on this one and the only choices I have are Virginia and Oregon
Instances
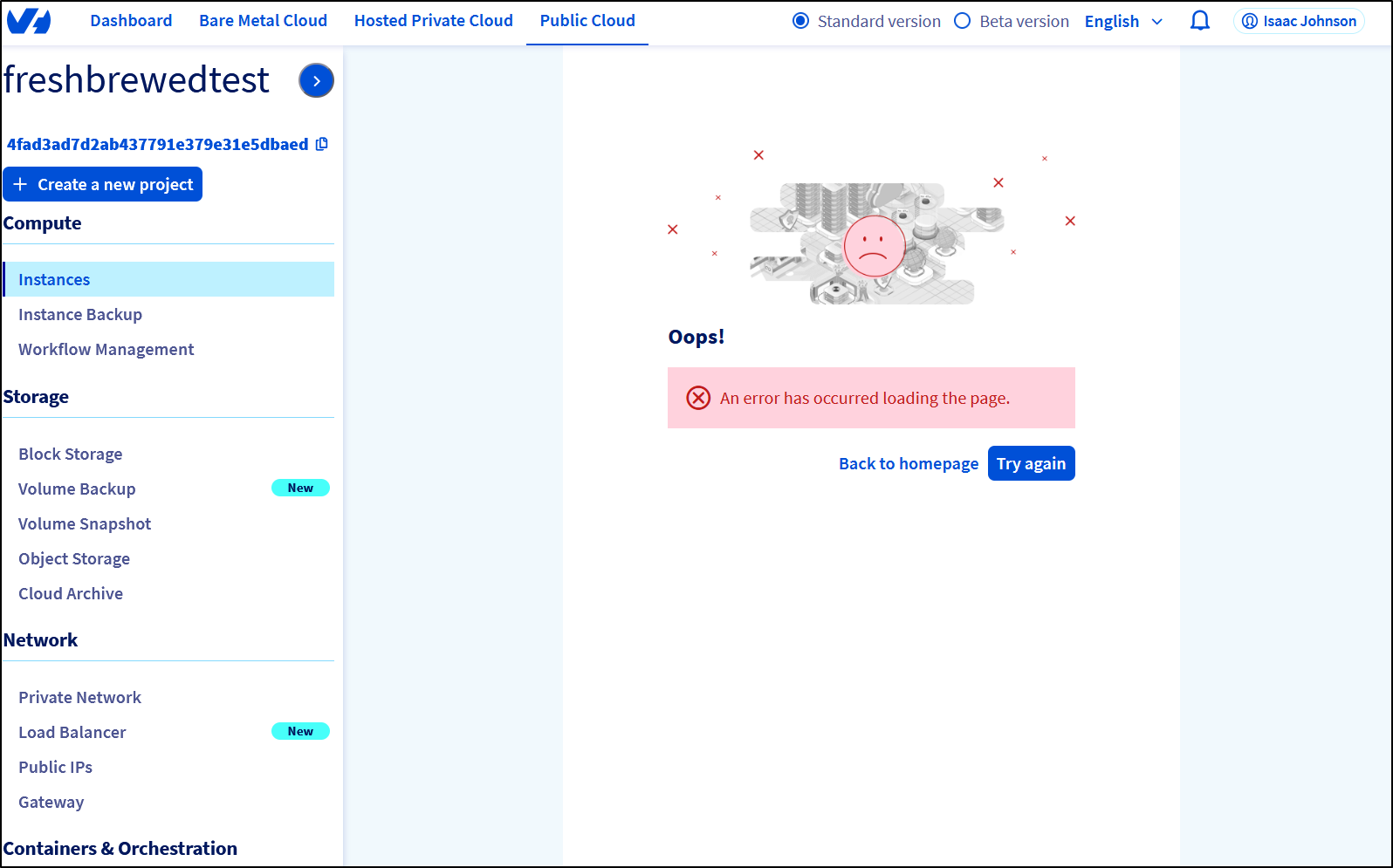
Soon, however, in just trying to find more items I got into an error loop in Firefox
I switched to Chrome and was unblocked, but again, as a US customer they just give me US otpions which I did not want.
The same was true of Kubernetes clusters
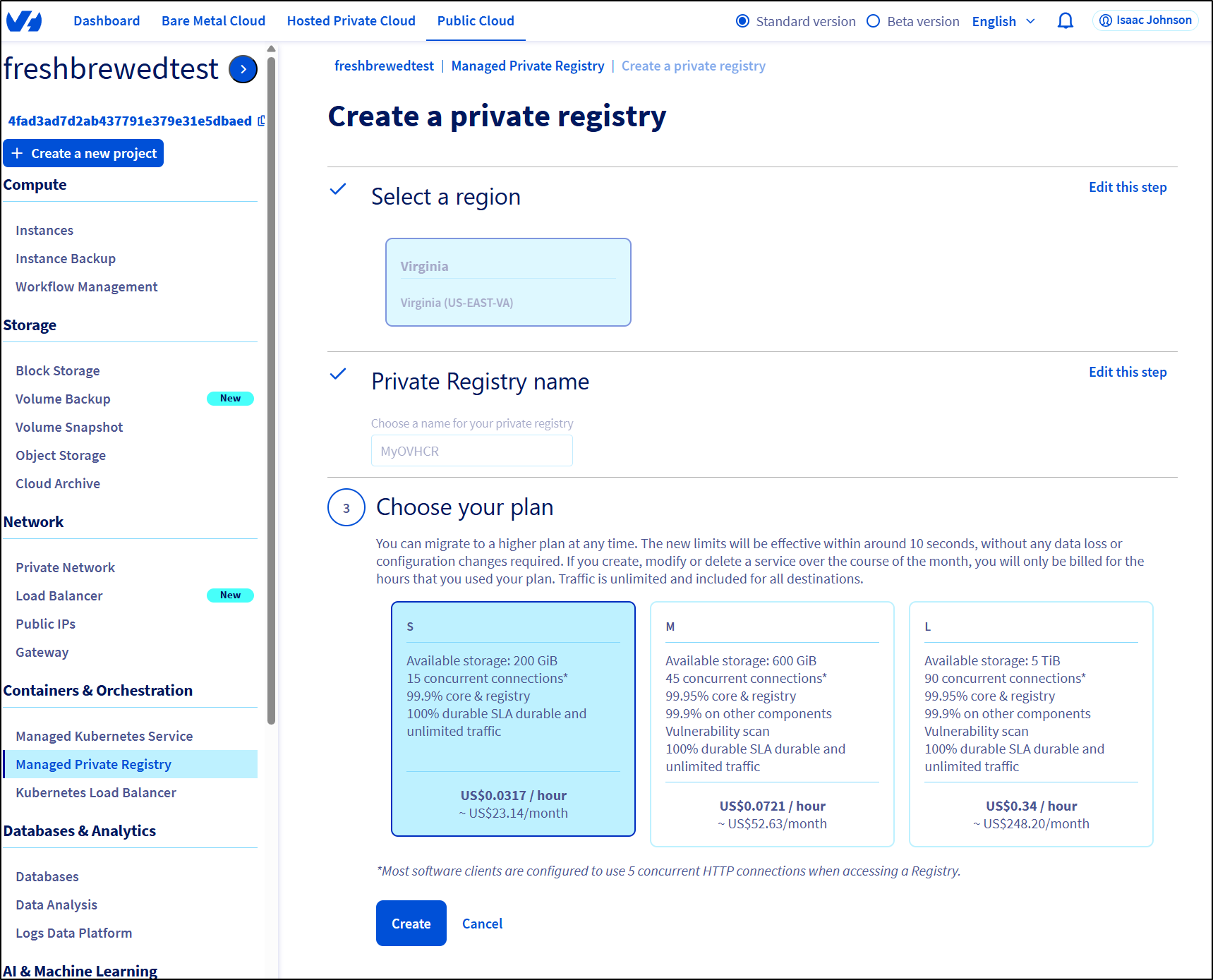
CRs
They had a basic “S”(small) container registry for US$23.14 a month which would not be too bad
Hetzner
We can signup for Hetzner at https://accounts.hetzner.com/signUp
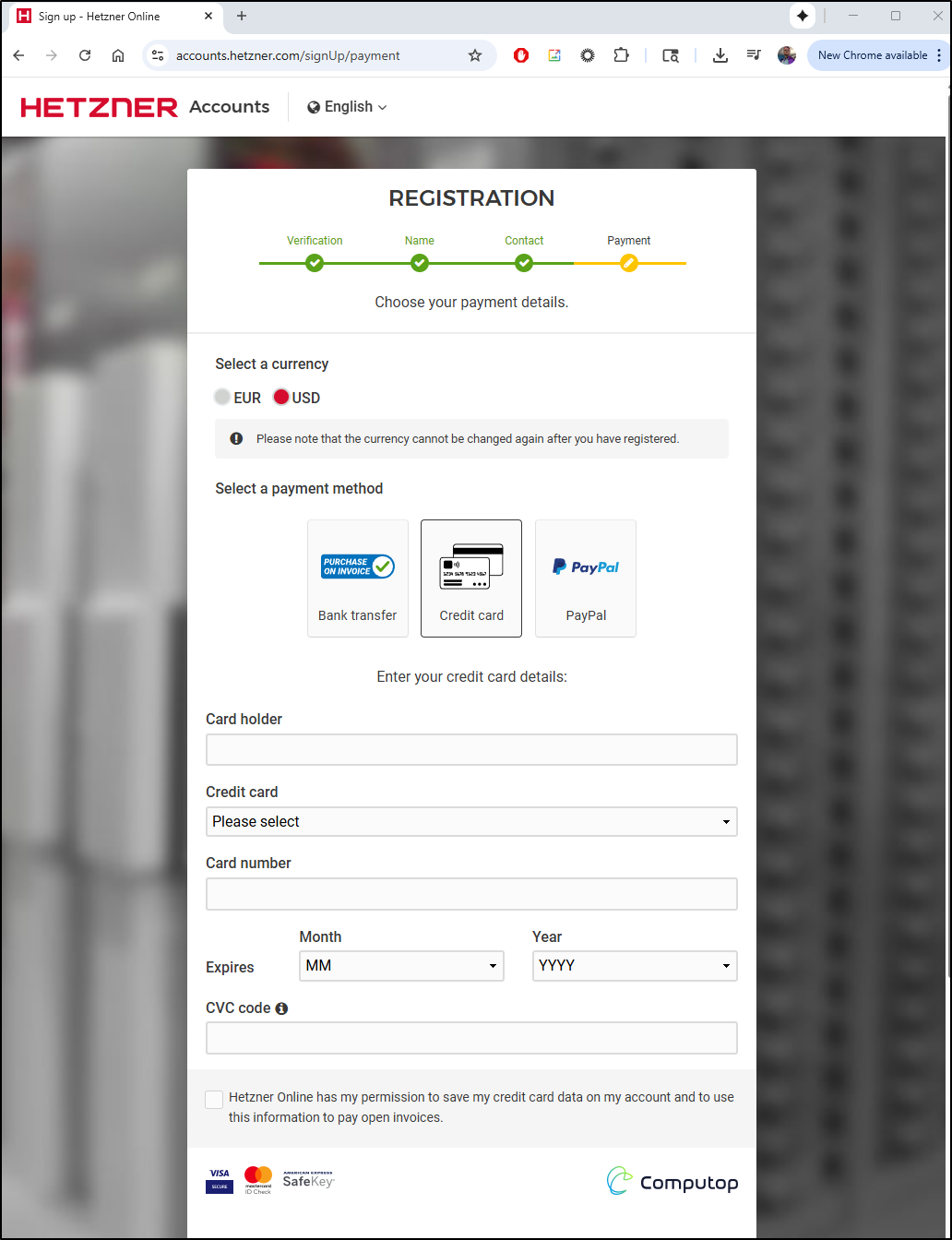
I then need to go through a signup flow
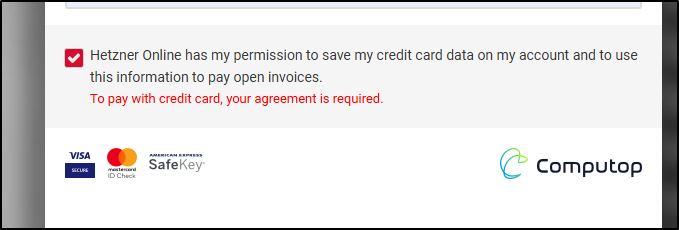
They don’t even let you get through the signup flow without a payment setup
I found it amusing they have an option to not save your card, but you cannot complete the form unless you agree to it
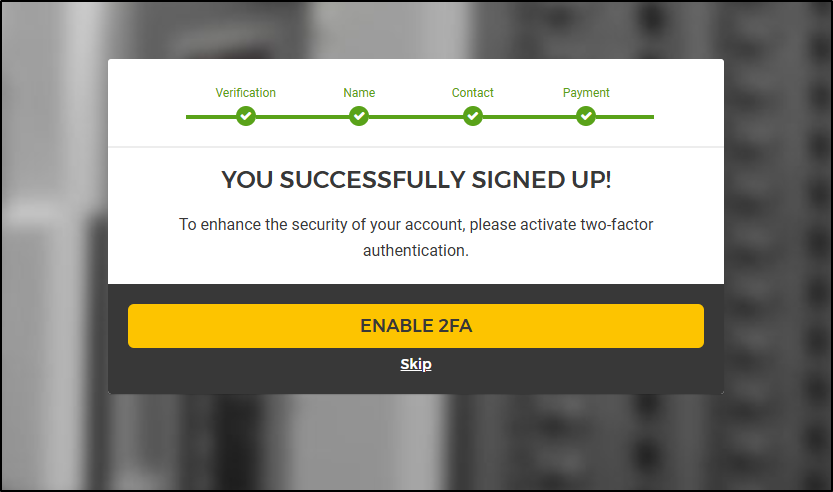
But then I can complete and enable MFA
Like IBM, they wanted “enhanced” verification of my identity.
But unlike IBM, they didn’t try to coax me into emailing full copies of my ID papers and instead has an app with a QR code that scanned my ID and then my face. I feel like I have done something like that before for some online certification exams.
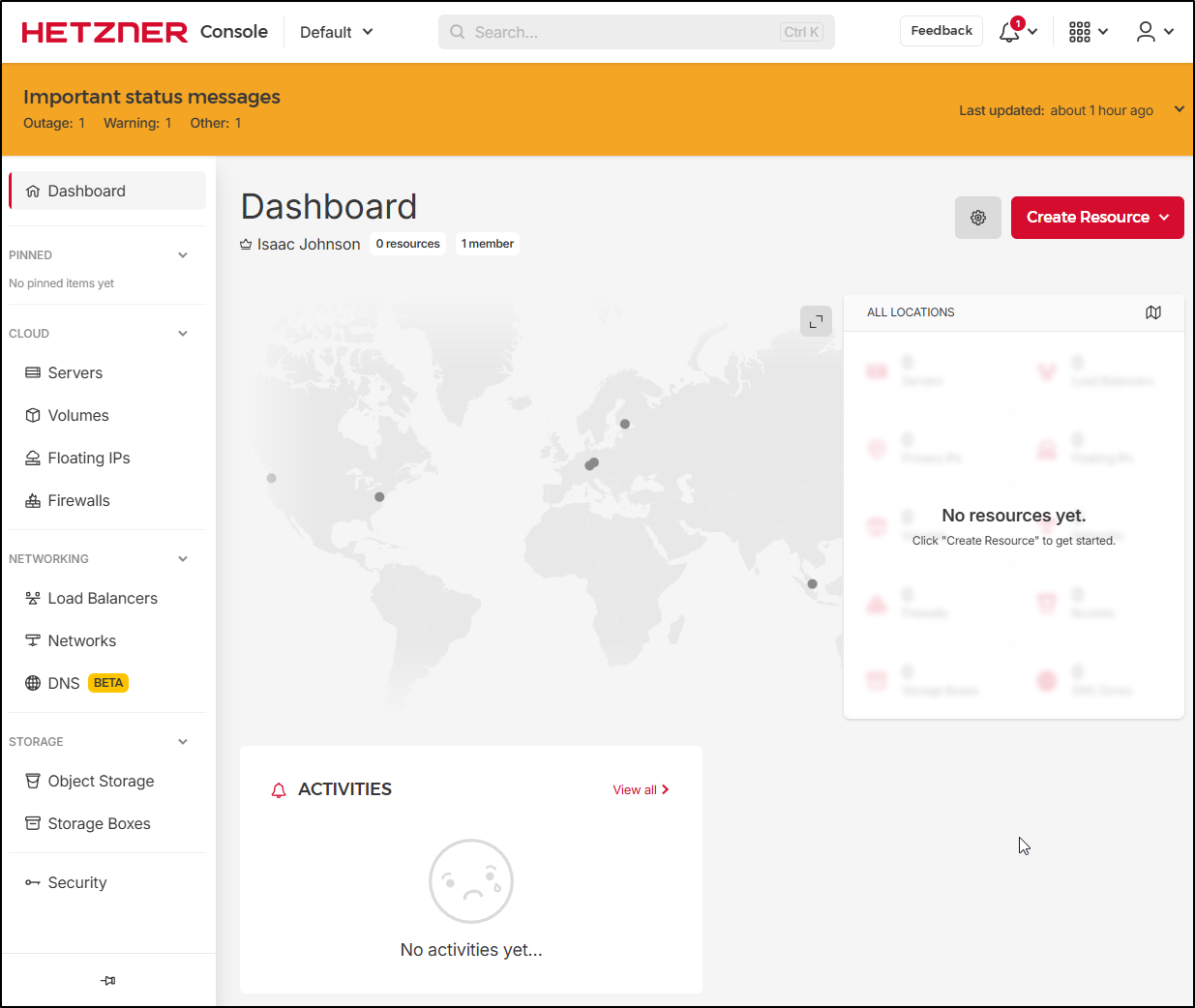
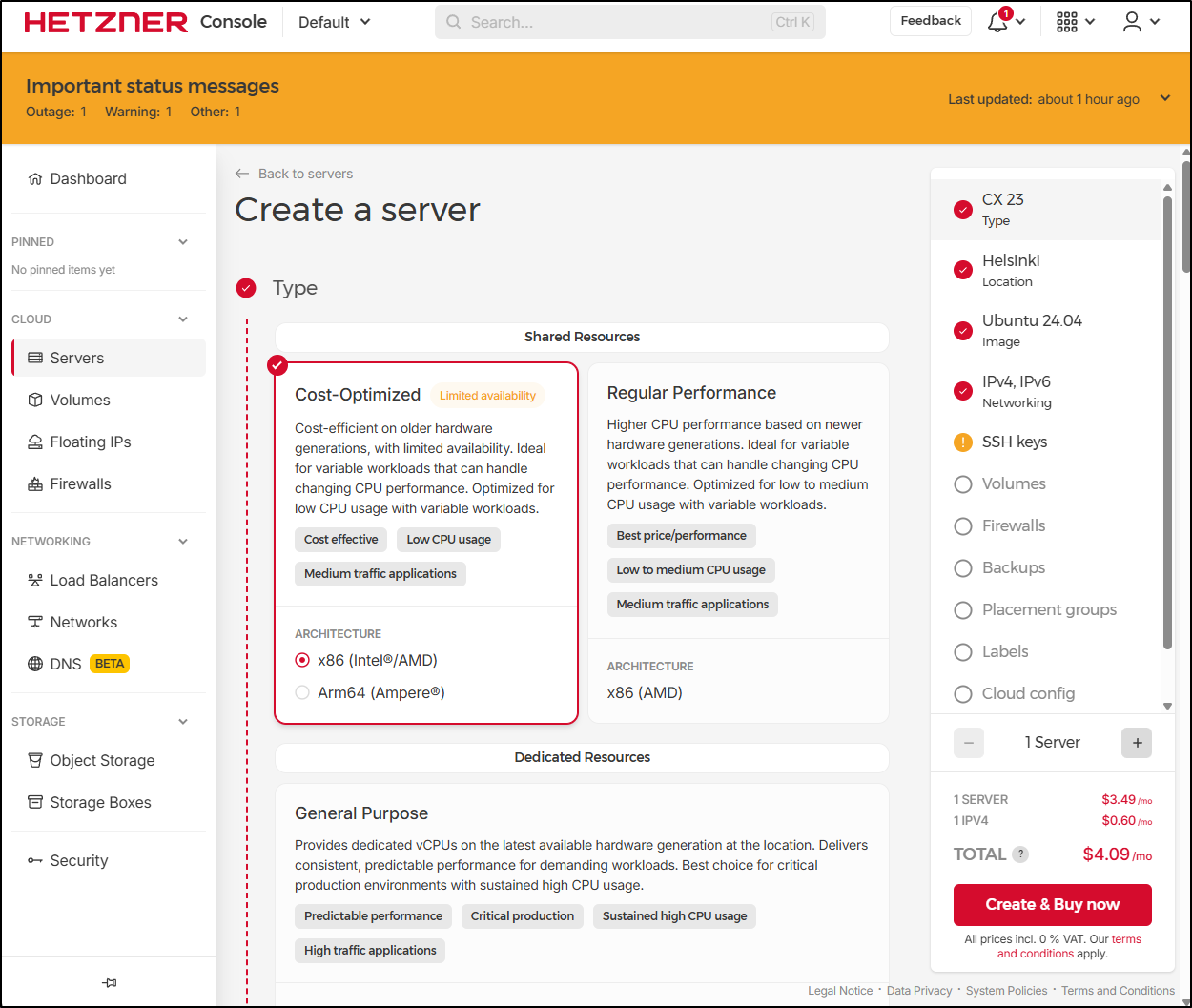
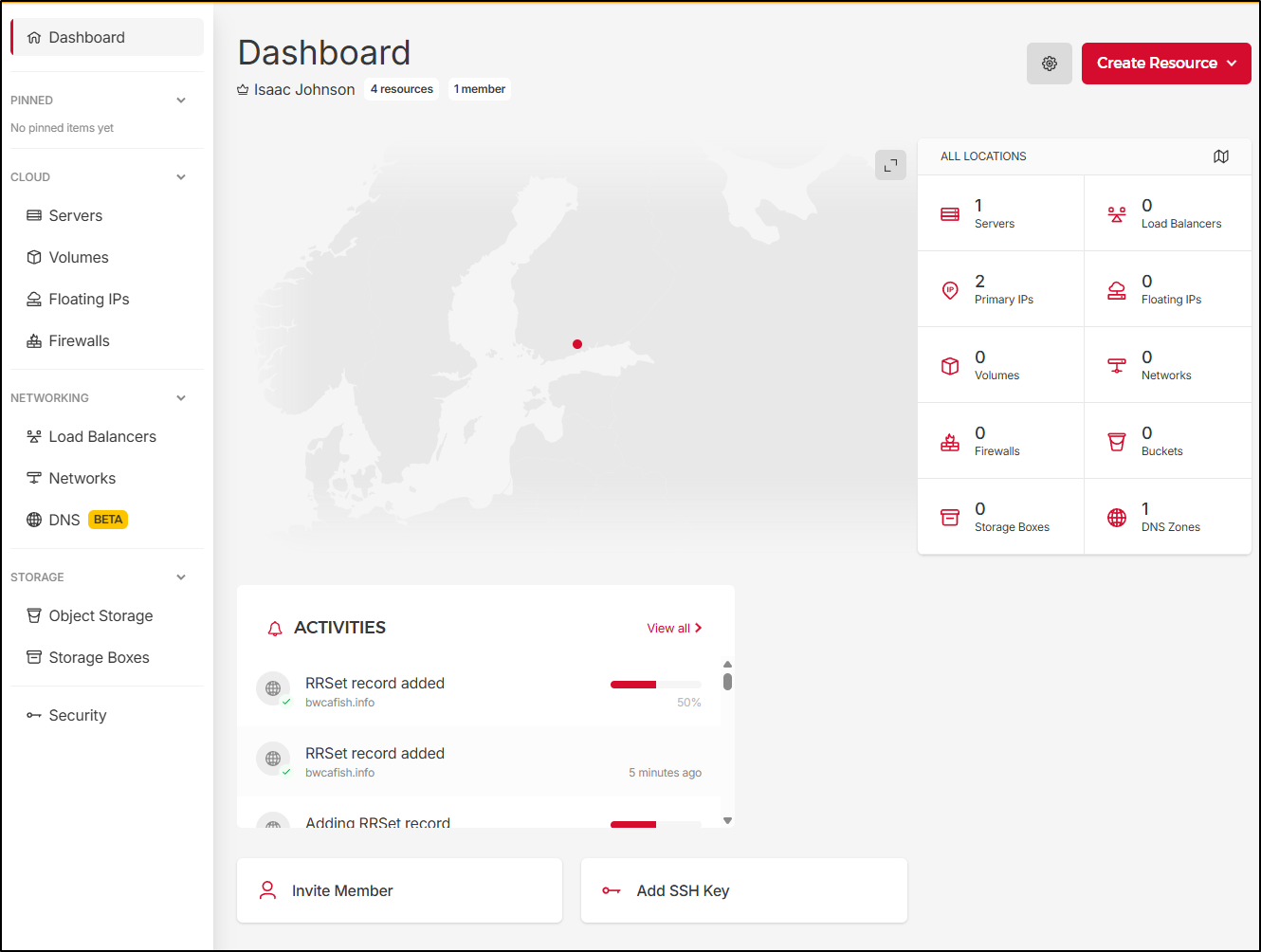
Once I got through, we can get to a Console landing page where we can create servers, firewalls, LBs and the like
Reviewing the server create page, it would seem that it’s pretty cheap for a basic VM, but I also think I’m signing up to pay for it all up front for a month
Let’s create a VM together and test it
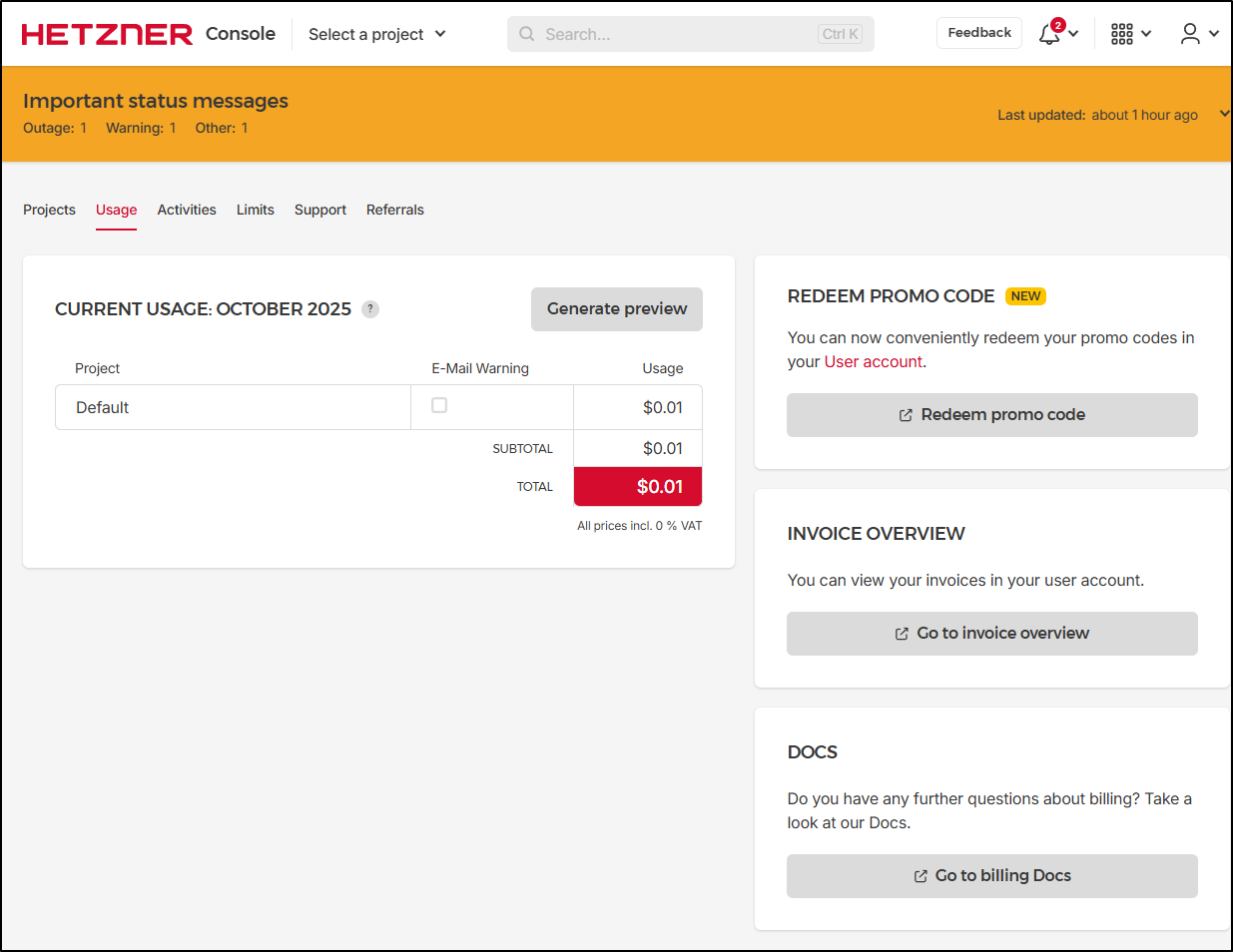
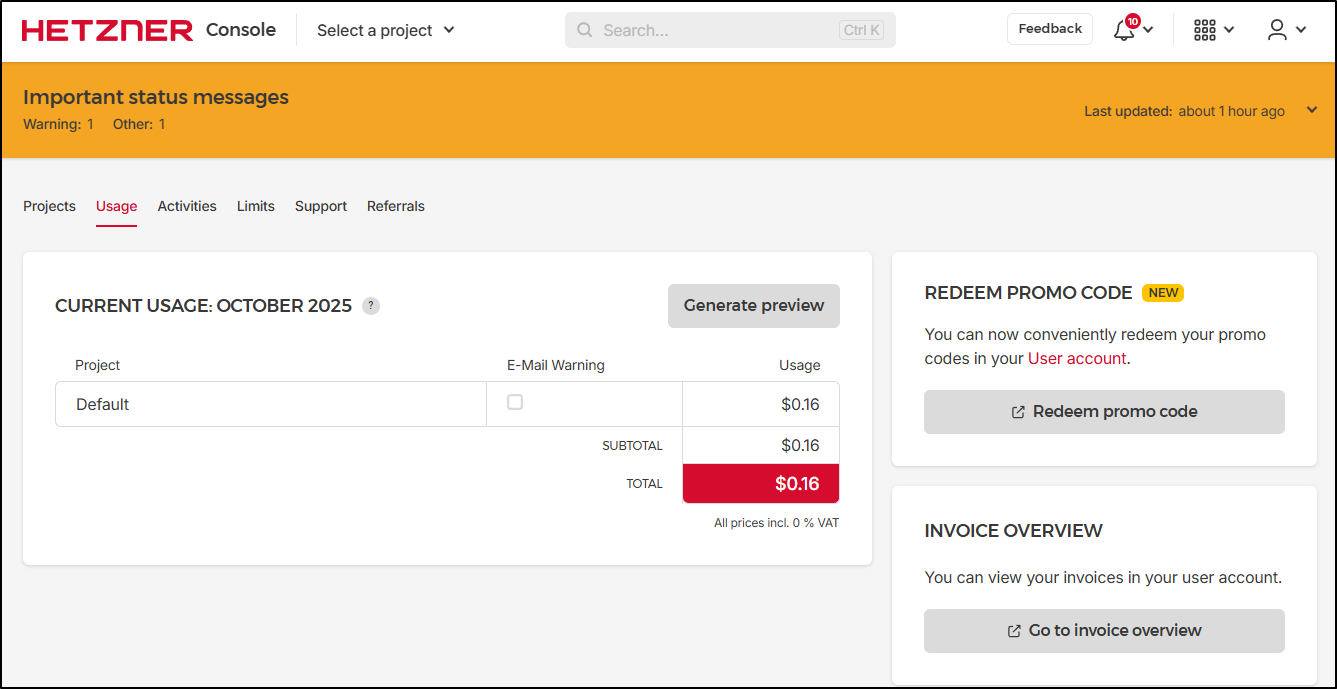
I went to check usage which suggests I just spent 1c
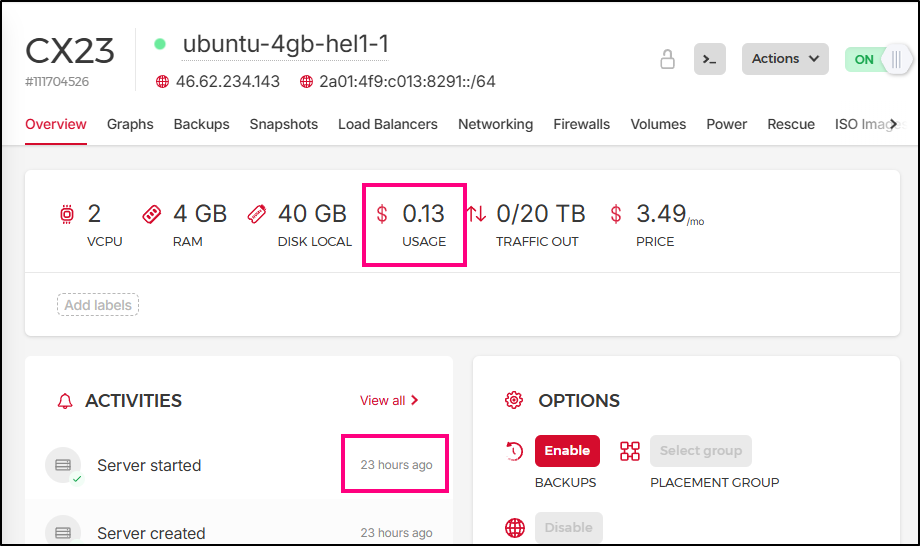
NOTE: I came back the next day and saw leaving it running a full day was about US$0.13
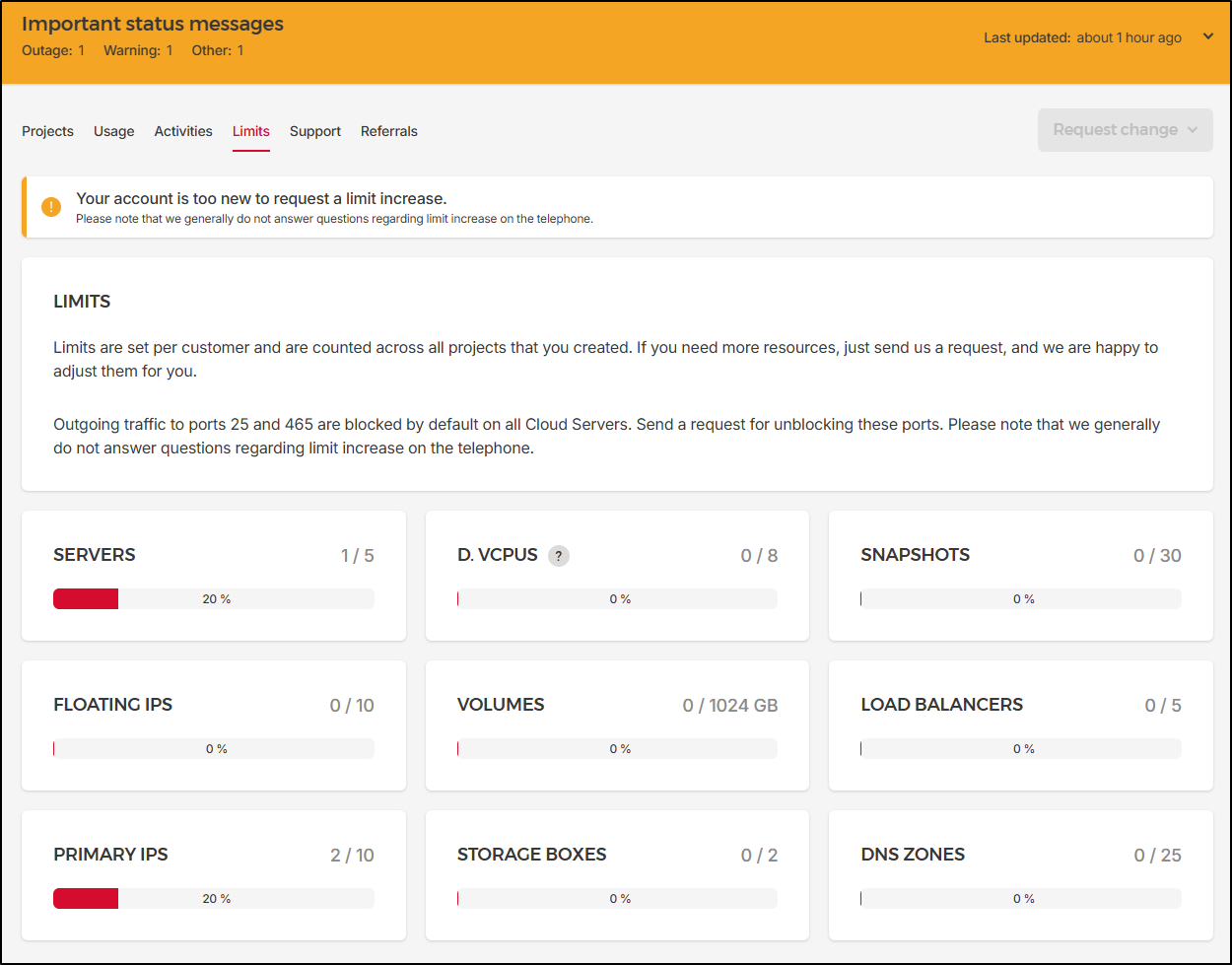
I saw Limits thinking it could be budget related, but instead are soft limits. I’m okay with most, but the 5 server limit is rather low IMHO for something I’m paying for.
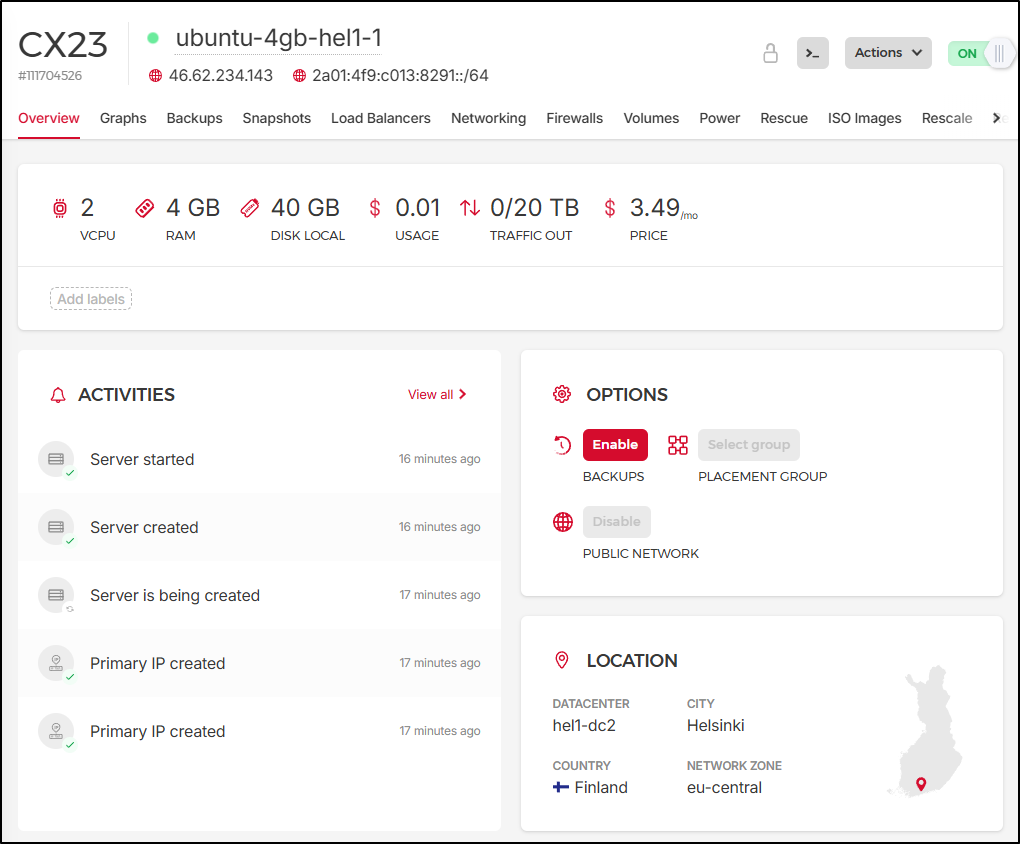
Going back to our server, we can see a history of activities, location and some specifics on usage like vCPU, RAM and disk
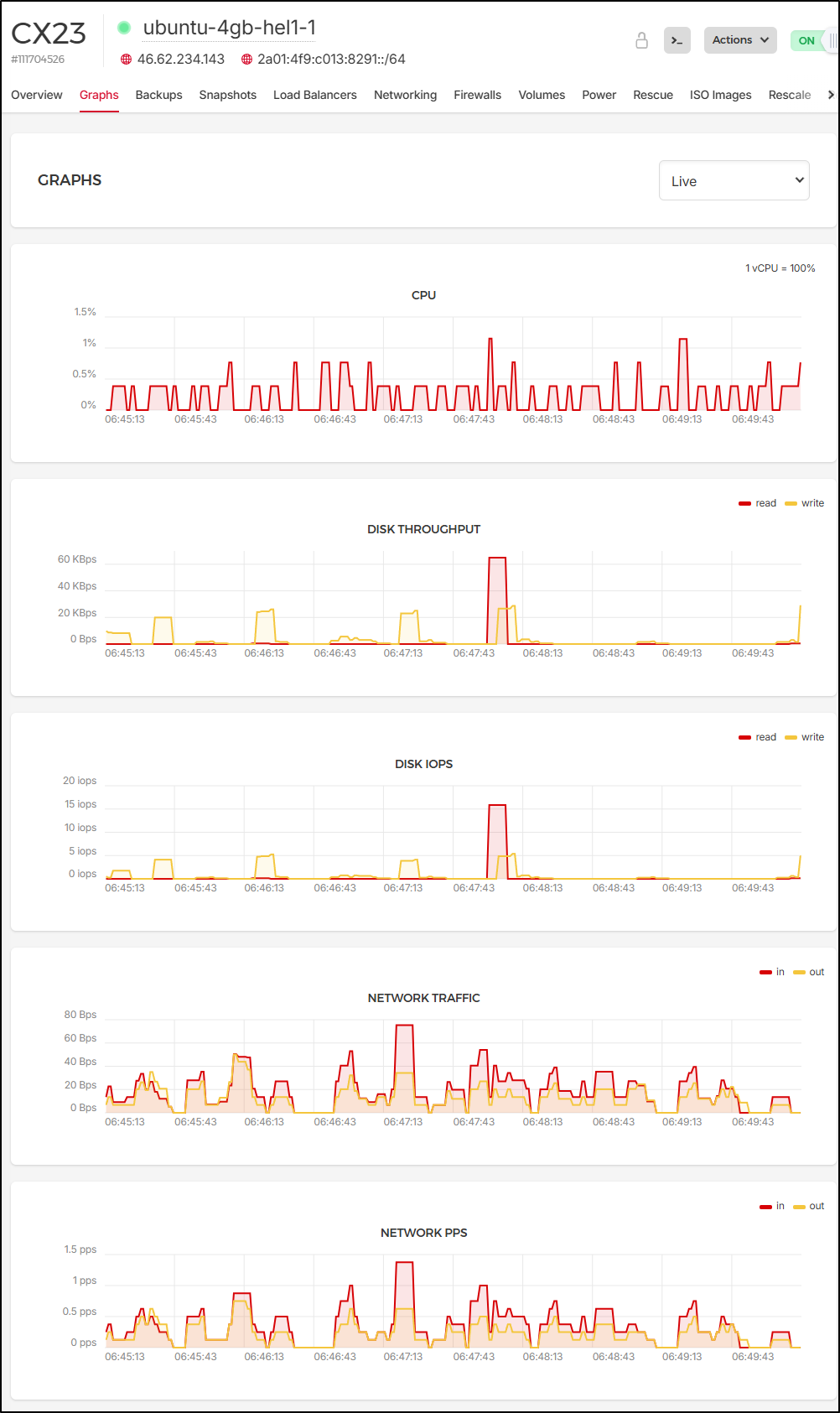
In “Graphs” we see some live metrics
Backups, as they suggest, enable automatic backups for 7 slots. They then add 20% to the cost of the server
Snapshots are point in time snaps of the disks for which you can create new servers (like a disk image capture)
Networking and Load Balancers let us assign an LB and Network to this host. I find this a pretty easy to grasp way to front traffic to some legacy services.
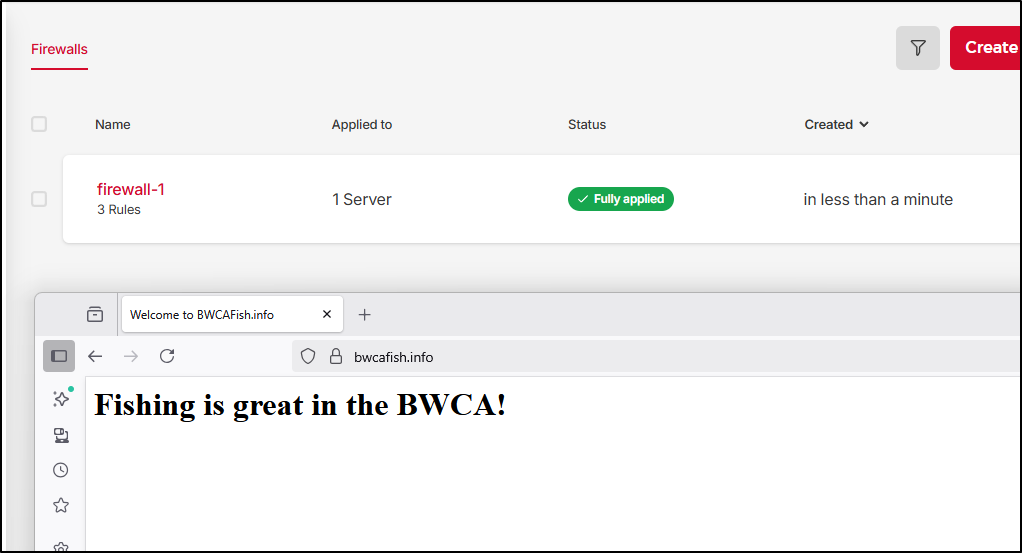
The firewall setup is a deny all except style
We can add multiple volumes (disk) to the host, each up to 10Tb
“Rescue” is a pretty cool option. Say you have a system in segfault or crashing at startup, you can mount the volume on another host to help sort the issues out. This would have come in real handy during the 2024 Crowdstrike issue
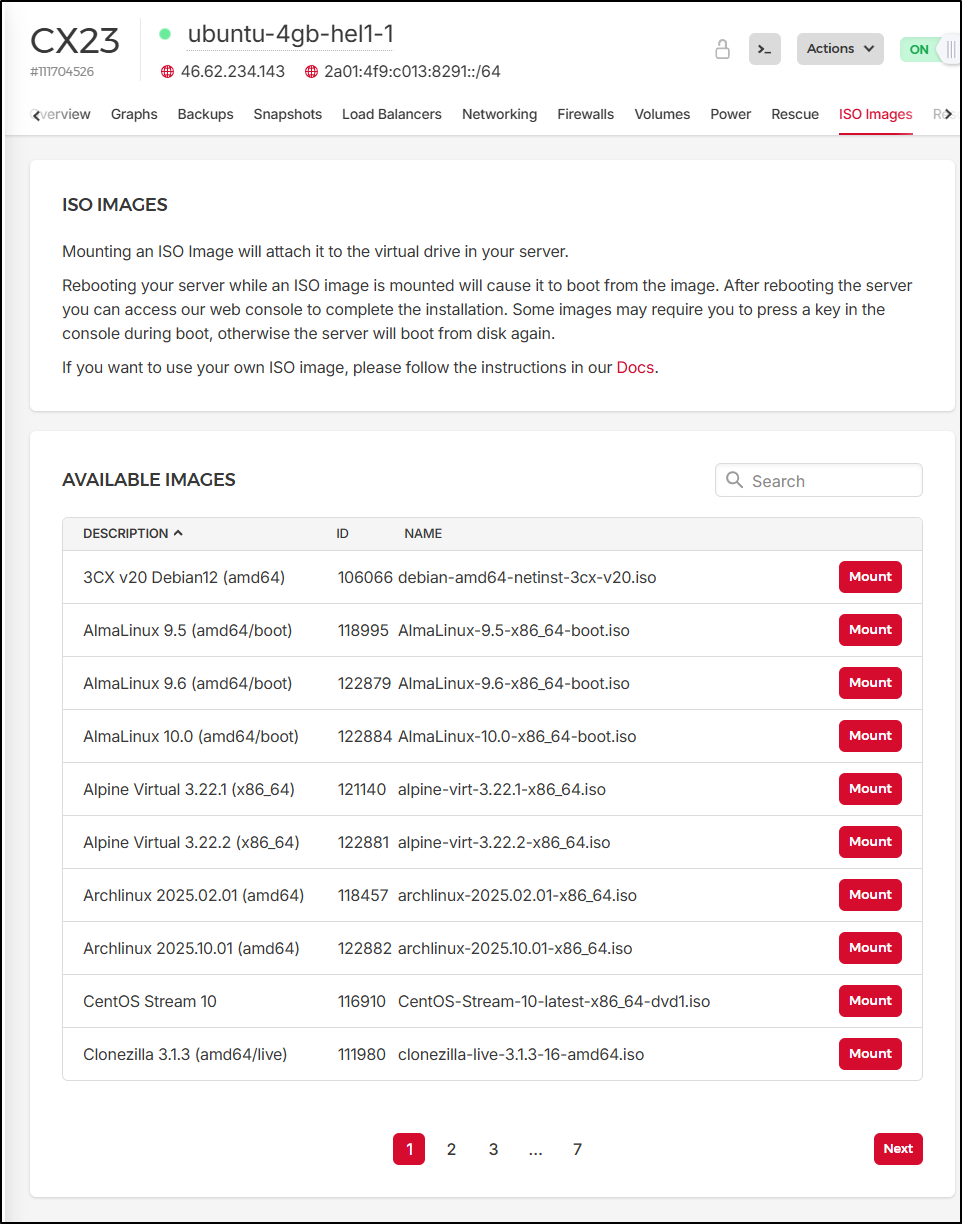
They let you mount some canned ISO images to the server. Not sure why this would be all that useful
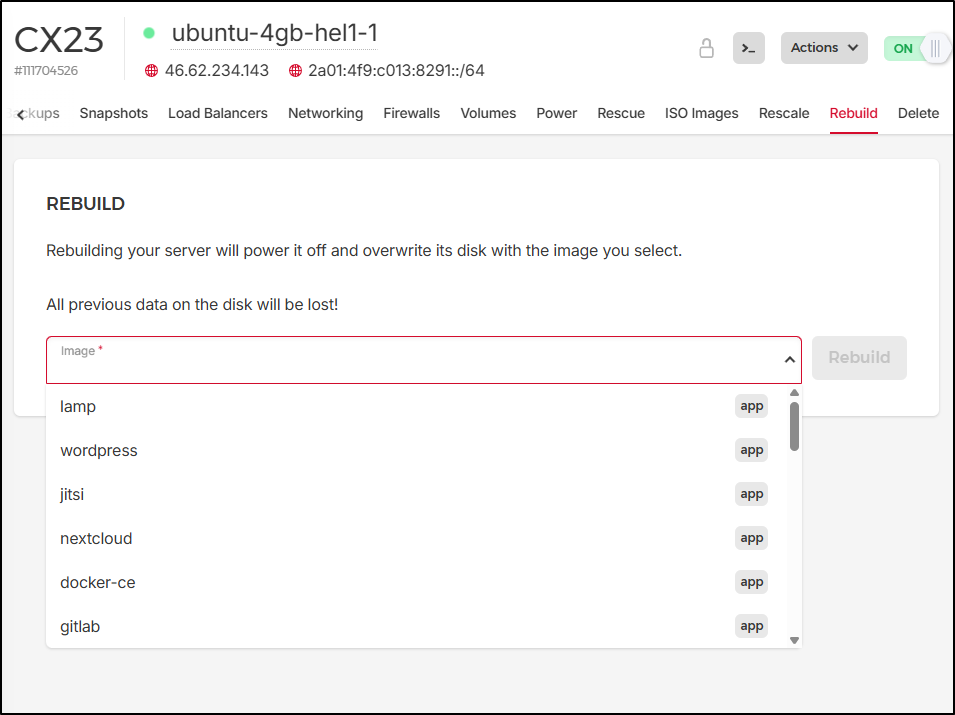
Rescale lets you change machine class and Rebuild looks like it lets you respin the host with a canned app
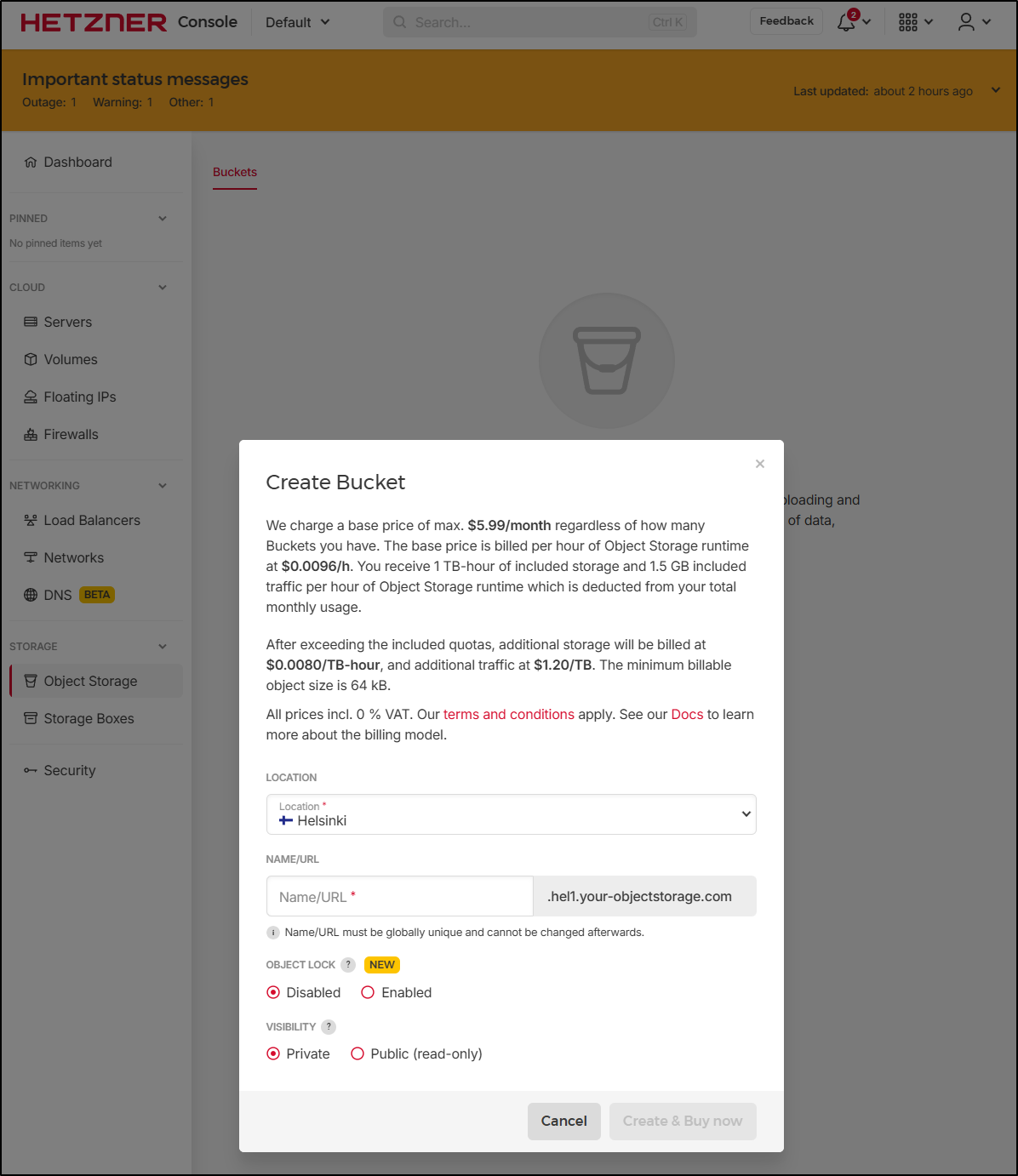
Object storage
It would seem I would spend about $6 month for buckets which has a lot of storage included
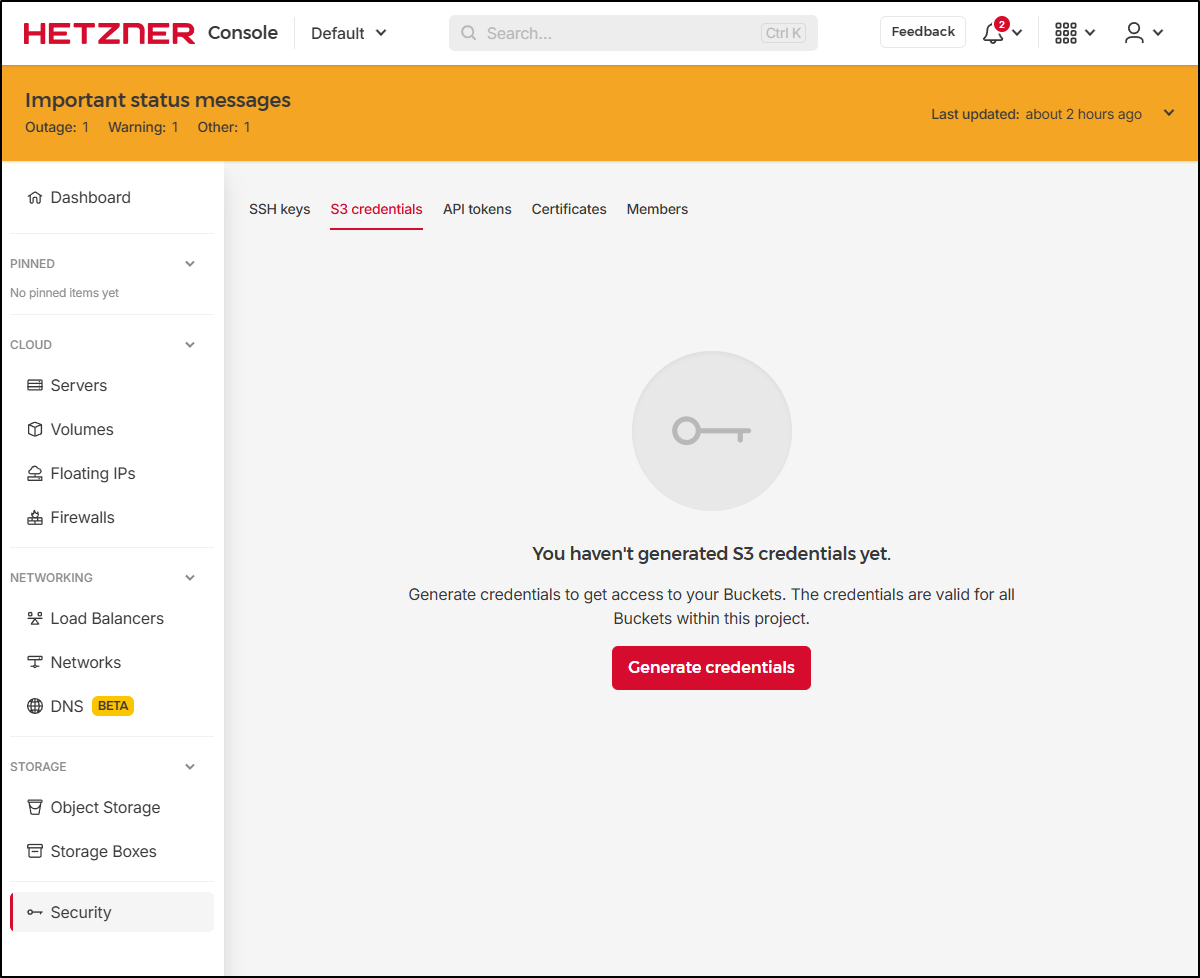
To access it, we could use an S3 compatible tools. To generate S3 credentials (access key and secret), we can do that in the Security/S3 credentials page
DNS Zone
I looked and looked, but all evidence seems to suggest that DNS management, at least for now, is completely free
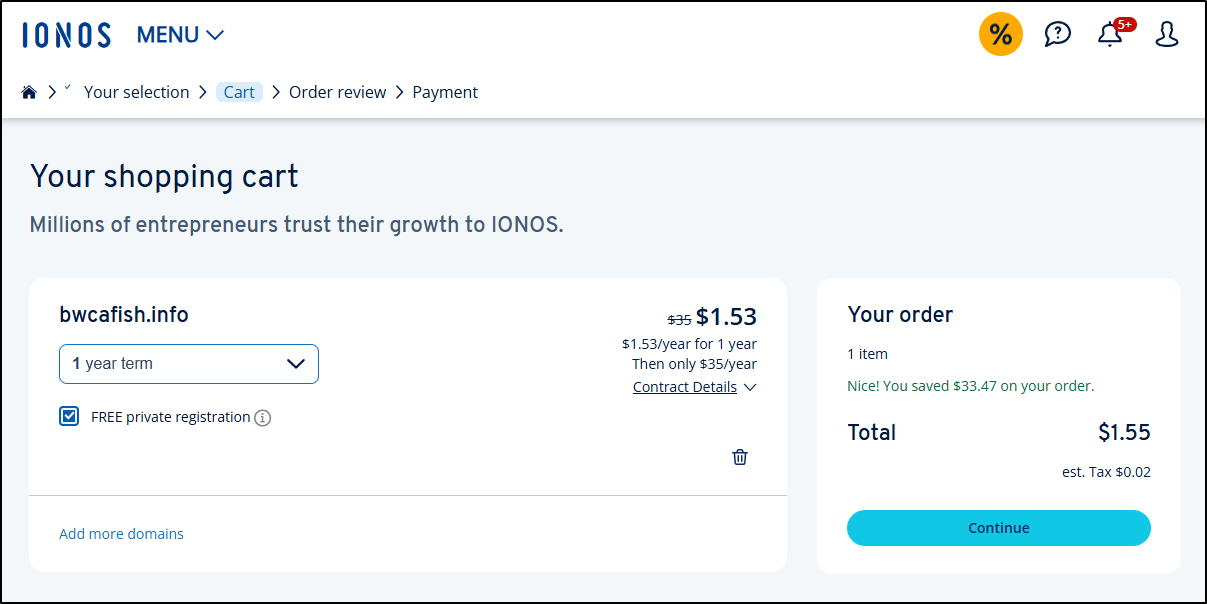
I want to test this so first I need a domain. I’ll use Ionos and get bwcafish.info
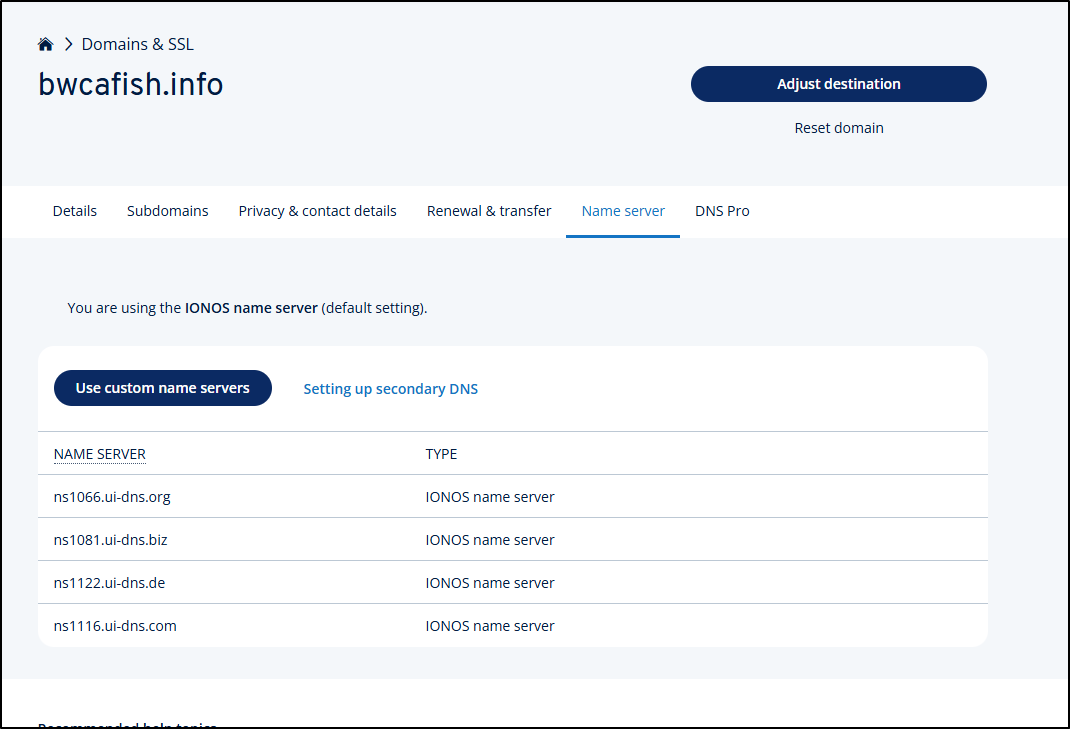
After I completed the order, it’s set to use IONOS name servers
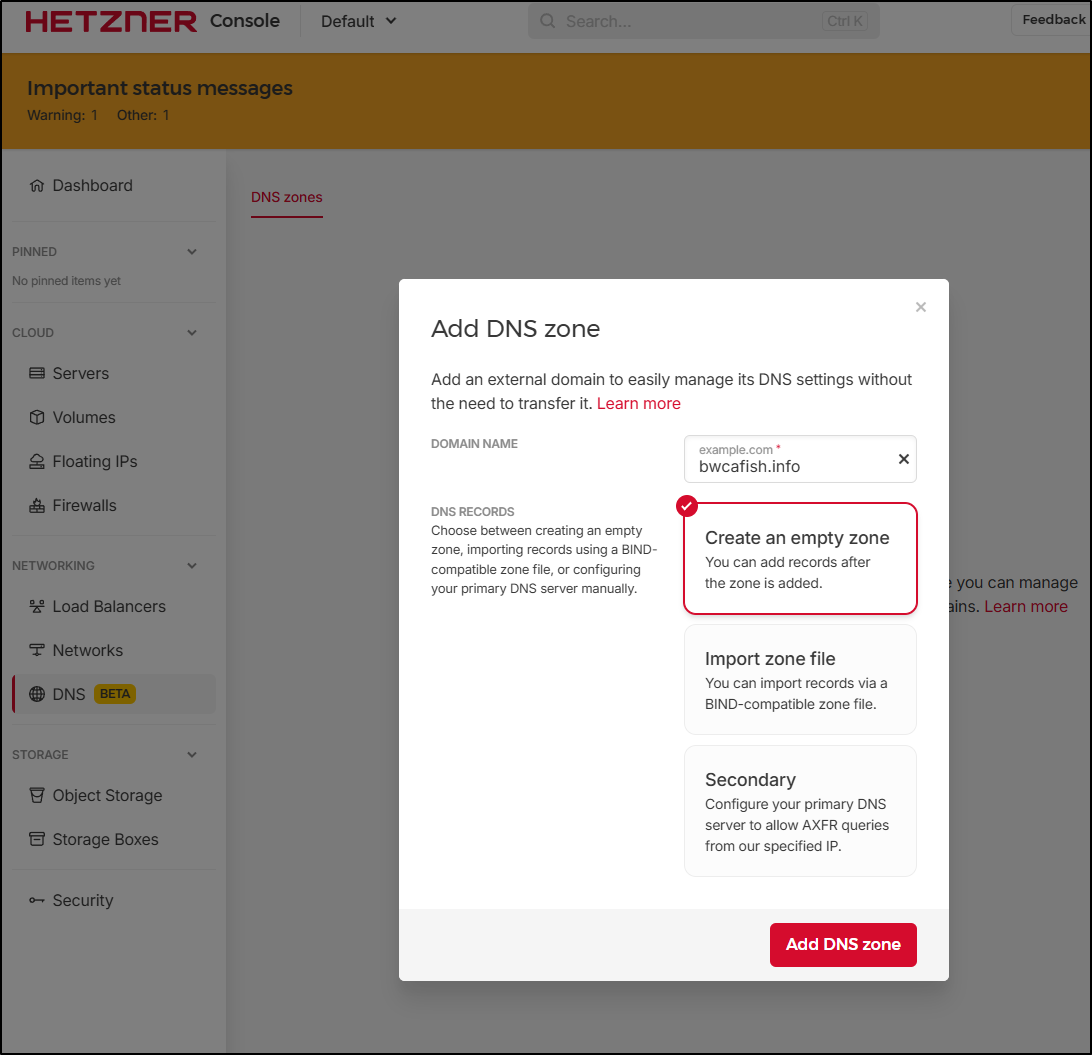
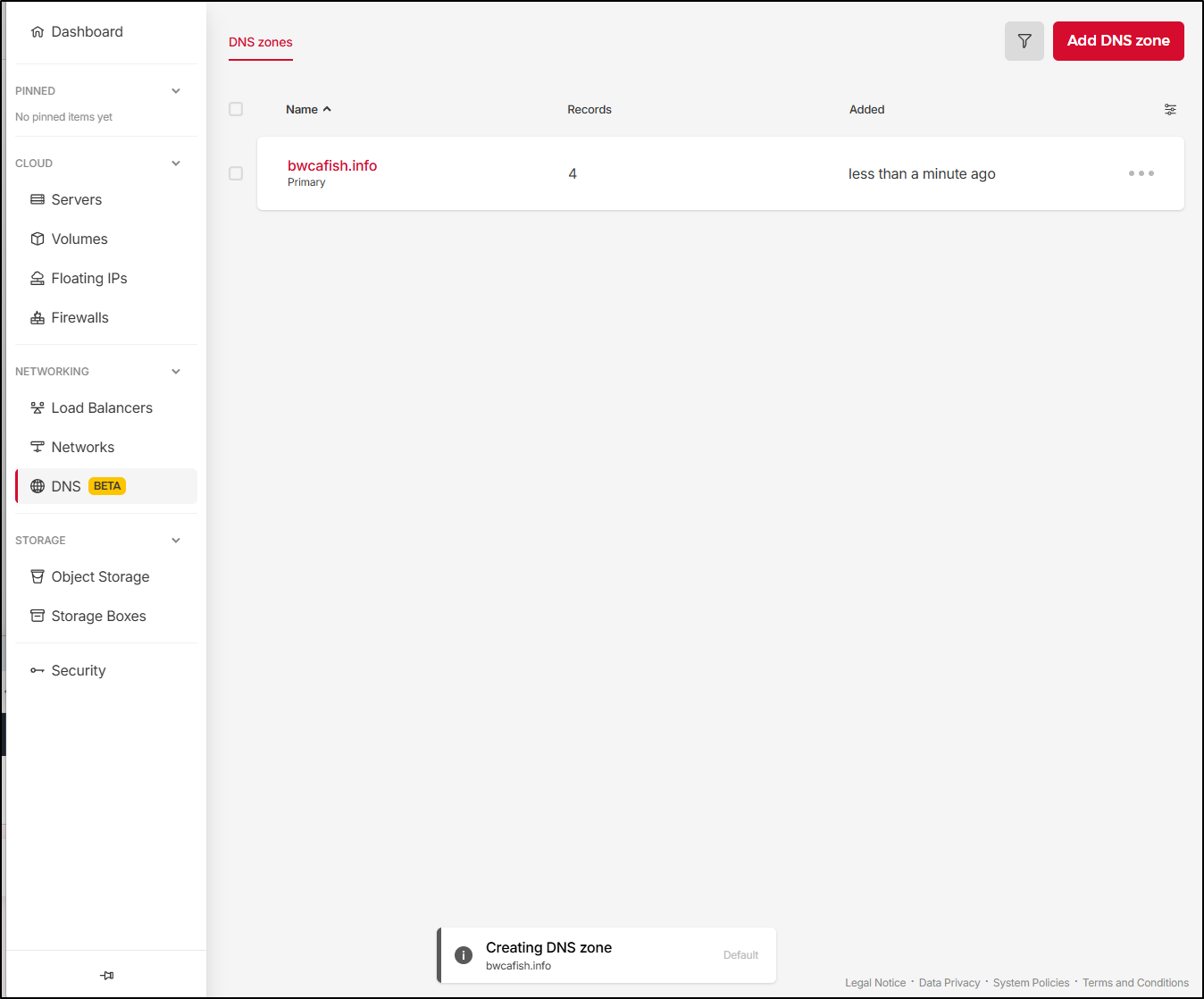
In Hetzner, I’ll add a new DNS zone
Which creates the zone
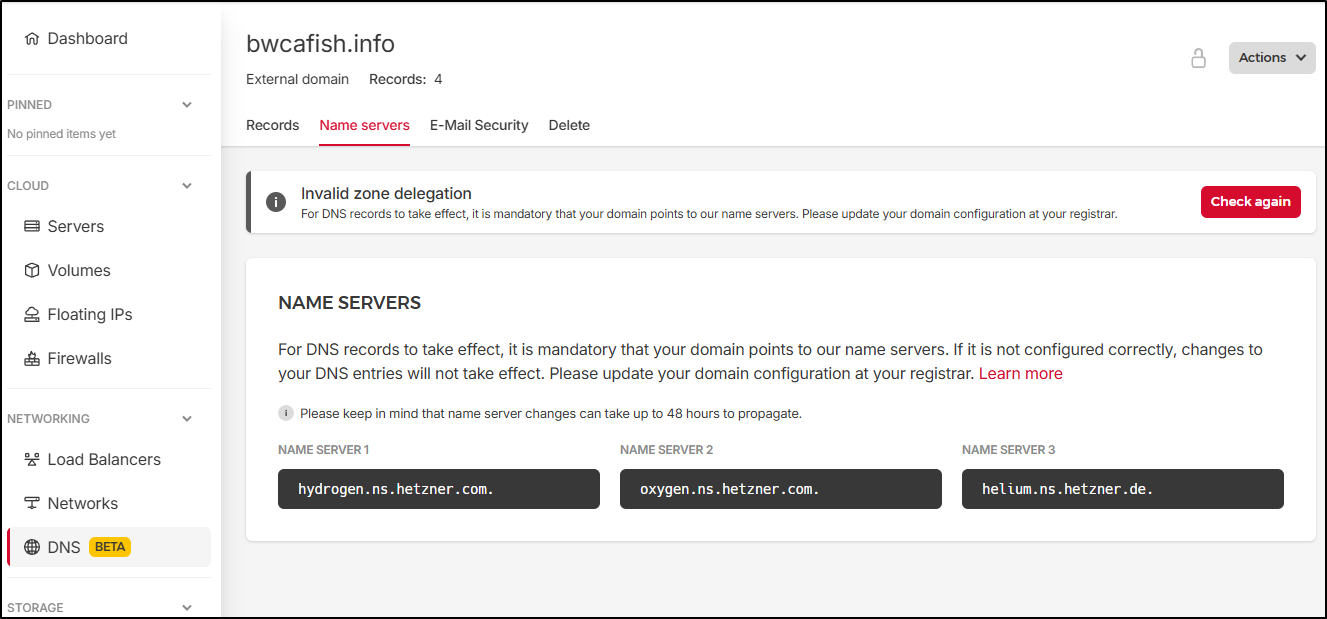
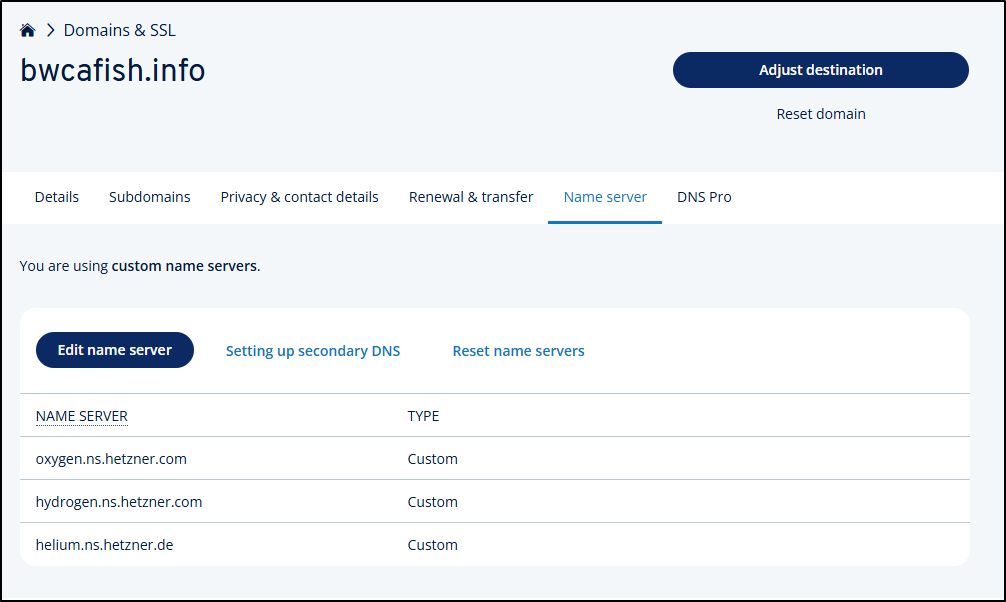
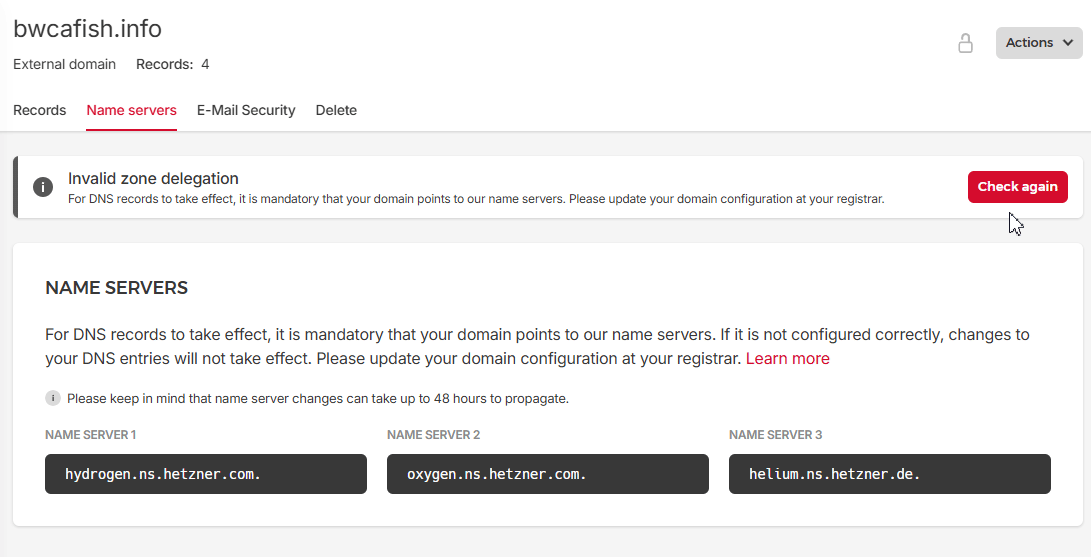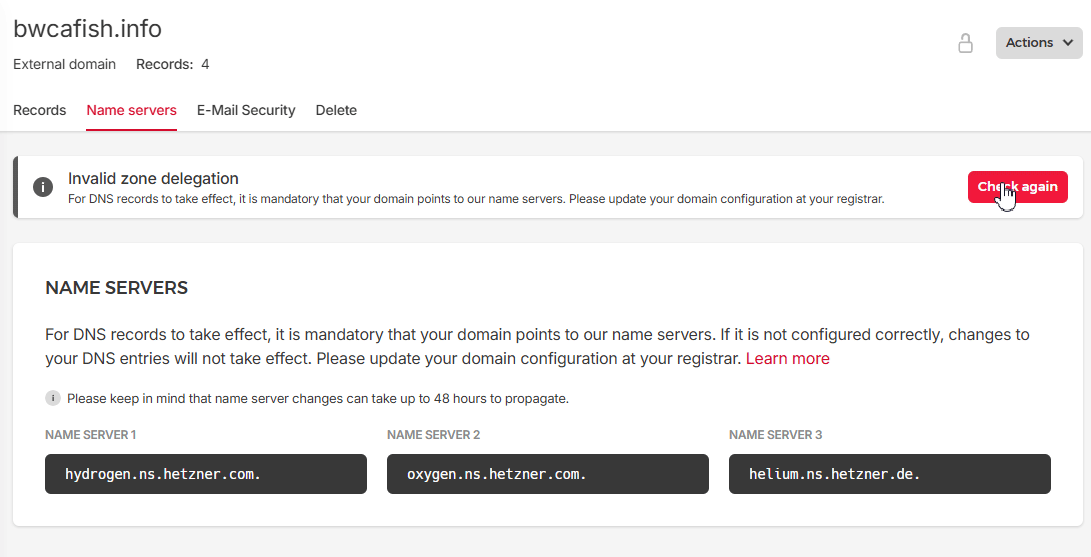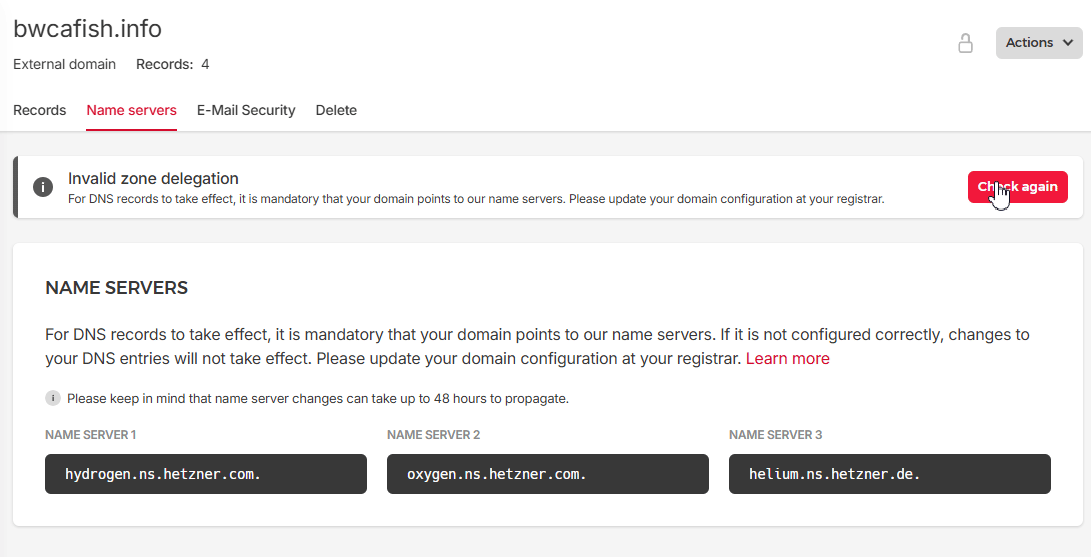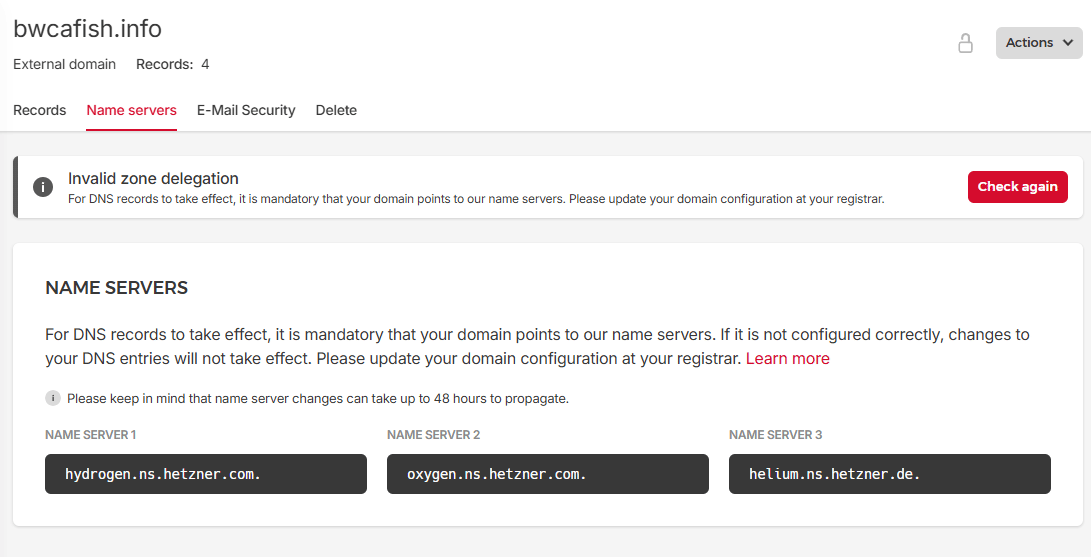
When I click on the zone we can see the error about “Invalid zone delegation”. We can see the name servers we should use in the “Name servers” section
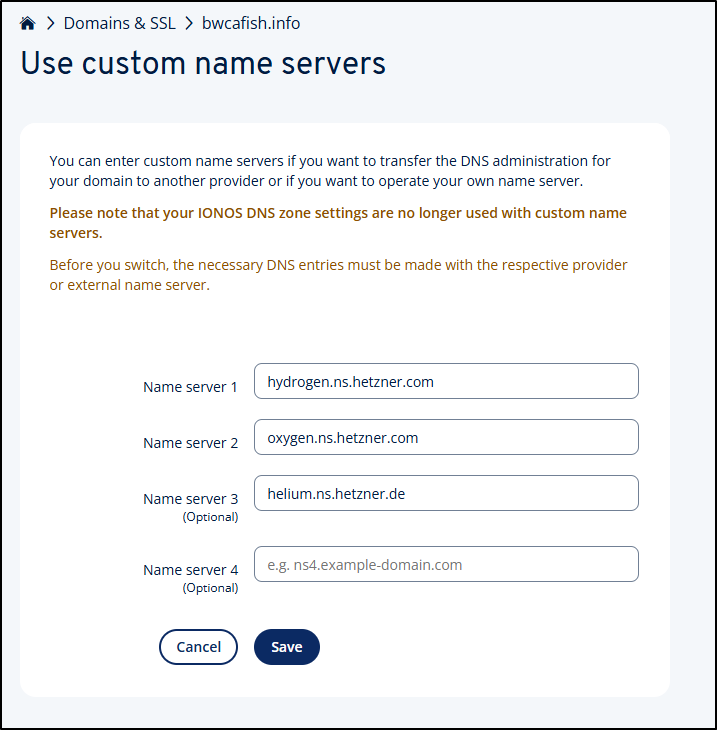
I’ll now update them in IONOS
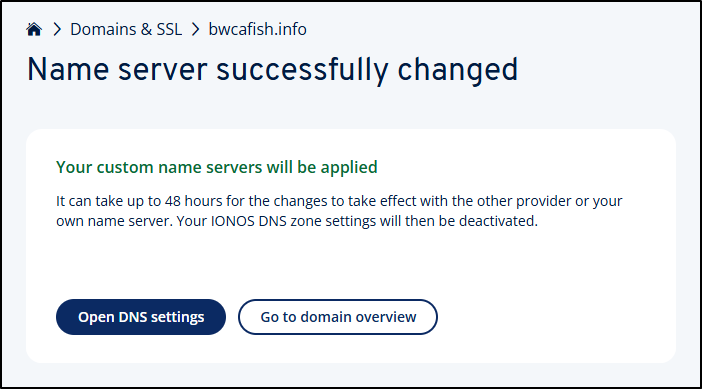
Once saved, we do see a notice it can take up to 2 days to apply
Though I can see IONOS now lists the Hetzner servers
I have found it takes a lot less time. I’ll just keep clicking “check again” in Hetzner till I see it clear
It took me about 12 minutes to clear that box
Let’s test it.
I’ll add Nginx to the VM still running
root@ubuntu-4gb-hel1-1:~# apt update && apt install nginx
Next, I need to update ufw (the Ubuntu Firewall) to allow HTTP and HTTPS traffic
root@ubuntu-4gb-hel1-1:~# ufw app list
Available applications:
Nginx Full
Nginx HTTP
Nginx HTTPS
OpenSSH
root@ubuntu-4gb-hel1-1:~# ufw allow 'Nginx HTTP'
Rules updated
Rules updated (v6)
root@ubuntu-4gb-hel1-1:~# ufw allow 'Nginx HTTPS'
Rules updated
Rules updated (v6)
I’ll make a basic HTML page to serve up
root@ubuntu-4gb-hel1-1:~# mkdir -p /var/www/bwcafish.info/html
root@ubuntu-4gb-hel1-1:~# ls -l /var/www/
total 8
drwxr-xr-x 3 root root 4096 Oct 29 11:24 bwcafish.info
drwxr-xr-x 2 root root 4096 Oct 29 11:18 html
root@ubuntu-4gb-hel1-1:~# vi /var/www/bwcafish.info/html/index.html
root@ubuntu-4gb-hel1-1:~# cat /var/www/bwcafish.info/html/index.html
<html>
<head>
<title>Welcome to BWCAFish.info</title>
</head>
<body>
<h1>Fishing is great in the BWCA!</h1>
</body>
</html>
I’m going to add a block to the default enabled site
root@ubuntu-4gb-hel1-1:~# cat /etc/nginx/sites-enabled/default | tail -n 13
server {
listen 443 ssl;
server_name bwcafish.info;
ssl_certificate /var/www/bwcafish.info/certificate.crt;
ssl_certificate_key /var/www/bwcafish.info/certificate.key;
location / {
root /var/www/bwcafish.info/html;
index index.html index.htm;
}
}
I’ll make a self-signed cert so Nginx is happy
root@ubuntu-4gb-hel1-1:~# sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /var/www/bwcafish.info/certificate.key -out /var/www/bwcafish.info/certific
ate.crt
...+.......+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*...+.........+......+.....+.......+.....+..........+..+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..+...+..+....+...+..+.................................+...+...................+.........+.........+.....+......+......+...+.+......+........+............+...............+...+.+..+....+...........+.......+...+..+......+.+.........+.....+..........+.................+...+.+.....+....+.........+..+.+..............+.........+.......+.........+.....+.+...+.....+............+....+......+..+...+...+.+...........+............+..........+.....+.......+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
..+.......+.....+............+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*........+...+......+.........+......+......+....+...+.....+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..+.+......+........+.+......+..+...+............+...+....+.........+.....+......+....+..+.......+..+..........+...+......+...........+....+...............+..+...+....+..+...+...+....+...+...+........+.......+..+...............+...+.......+...+..+......+.+...............+......+...............+........+.+...+......+..+..........+..............+...+..........+........+...+.+.....+....+...........+...+...+...+....+...........+............+.............+..+.......+......+..............+.+......+.....+..........+.....+.+..+.+.........+.....+...+...+....+........+.......+.....+.......+...+..+..........+...+.....+...+...+......+....+.....+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:MN
Locality Name (eg, city) []:Woodbury
Organization Name (eg, company) [Internet Widgits Pty Ltd]:BWCAFish
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:Isaac Johnson
Email Address []:isaac.johnson@gmail.com
Then restart Nginx. I use status to make sure I didn’t make any typos in the conf or use the wrong location for the certs
root@ubuntu-4gb-hel1-1:~# service nginx restart
root@ubuntu-4gb-hel1-1:~# service nginx status
● nginx.service - A high performance web server and a reverse proxy server
Loaded: loaded (/usr/lib/systemd/system/nginx.service; enabled; preset: enabled)
Active: active (running) since Wed 2025-10-29 12:03:55 UTC; 6s ago
Docs: man:nginx(8)
Process: 20435 ExecStartPre=/usr/sbin/nginx -t -q -g daemon on; master_process on; (code=exited, status=0/SUCCESS)
Process: 20437 ExecStart=/usr/sbin/nginx -g daemon on; master_process on; (code=exited, status=0/SUCCESS)
Main PID: 20438 (nginx)
Tasks: 3 (limit: 4540)
Memory: 2.7M (peak: 3.0M)
CPU: 67ms
CGroup: /system.slice/nginx.service
├─20438 "nginx: master process /usr/sbin/nginx -g daemon on; master_process on;"
├─20439 "nginx: worker process"
└─20440 "nginx: worker process"
Oct 29 12:03:55 ubuntu-4gb-hel1-1 systemd[1]: Starting nginx.service - A high performance web server and a reverse proxy server...
Oct 29 12:03:55 ubuntu-4gb-hel1-1 systemd[1]: Started nginx.service - A high performance web server and a reverse proxy server.
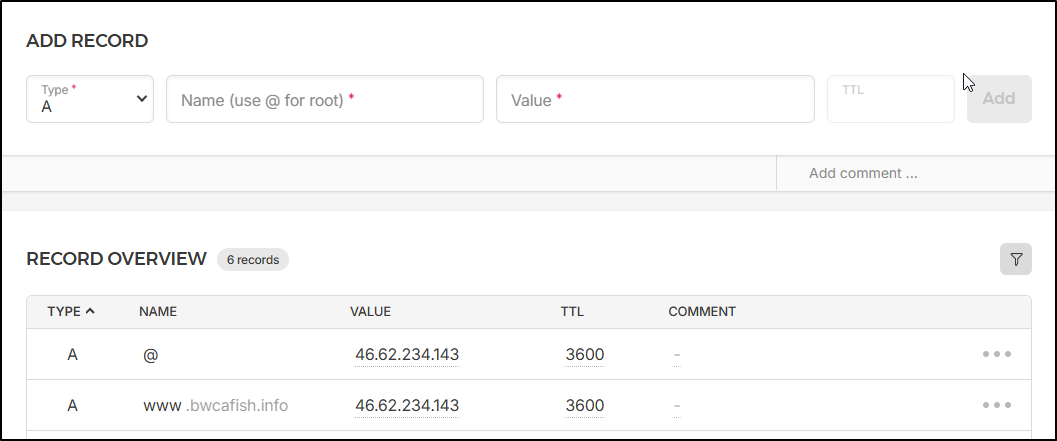
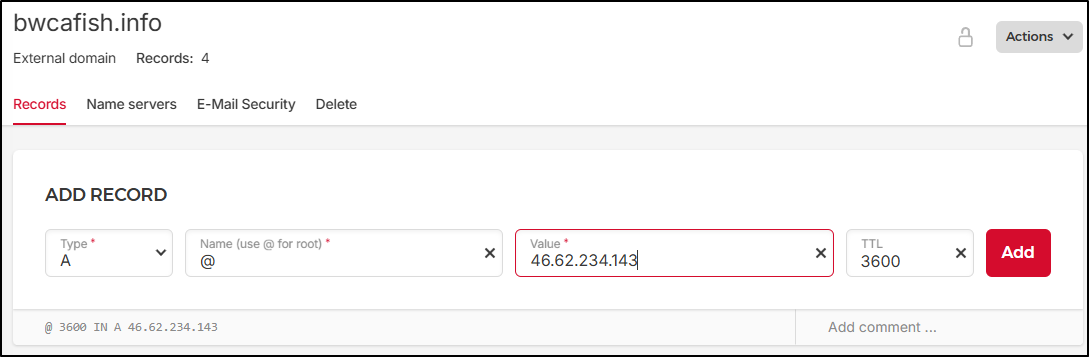
Back in the DNS Zone, I’ll make two A records - one for “www” and one without. I’m using the IP of my VM for the value
Note: you need to use @ for the root
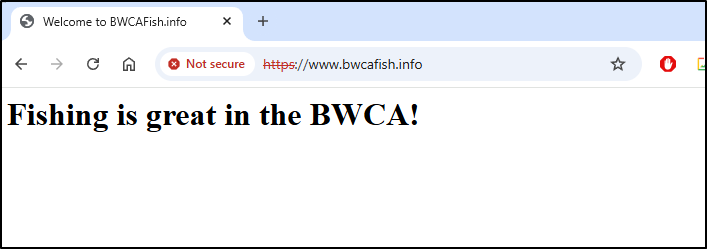
And now we can see that https://bwcafish.info works, albeit with a self-signed cert (which always annoys the web browser)
Our next step is to get certbot. This is similar to cert-manager in Kubernetes
root@ubuntu-4gb-hel1-1:~# apt install certbot python3-certbot-nginx
We can now use certbot to get real certificates
root@ubuntu-4gb-hel1-1:~# certbot --nginx -d bwcafish.info -d www.bwcafish.info
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): isaac.johnson@gmail.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.5-February-24-2025.pdf. You must
agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Account registered.
Requesting a certificate for bwcafish.info and www.bwcafish.info
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/bwcafish.info/fullchain.pem
Key is saved at: /etc/letsencrypt/live/bwcafish.info/privkey.pem
This certificate expires on 2026-01-27.
These files will be updated when the certificate renews.
Certbot has set up a scheduled task to automatically renew this certificate in the background.
Deploying certificate
Successfully deployed certificate for bwcafish.info to /etc/nginx/sites-enabled/default
Successfully deployed certificate for www.bwcafish.info to /etc/nginx/sites-enabled/default
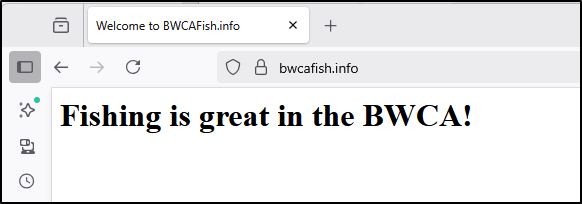
Congratulations! You have successfully enabled HTTPS on https://bwcafish.info and https://www.bwcafish.info
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
We can now see a valid website with HTTPS served out of Hetzner
This means I have just one server running and a free DNS zone
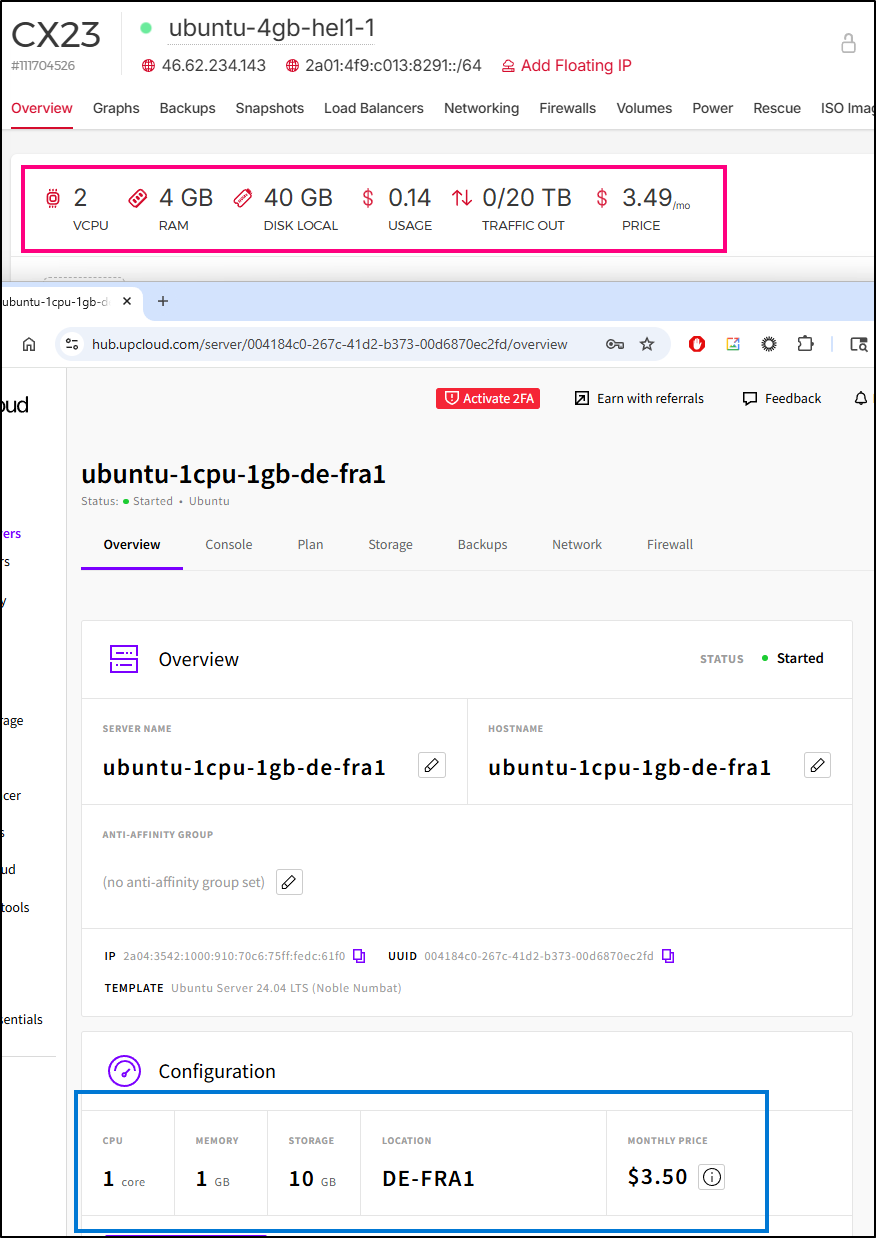
I’m on track to spend about $3.50 a month for this - less than a cup of Starbucks
Where I find this a bit more exciting is that 2vCPU/4Gb box, while small, should be enough to run a NodeJS or Python server without issue - it could be a very easy way to host a demo app. It might be a tad small for Docker, but a Python-slim container could run in those limits.
This is where, while I really like UpCloud, the Hetzner option is a bit better deal:
(red is Hetzner and blue is UpCloud)
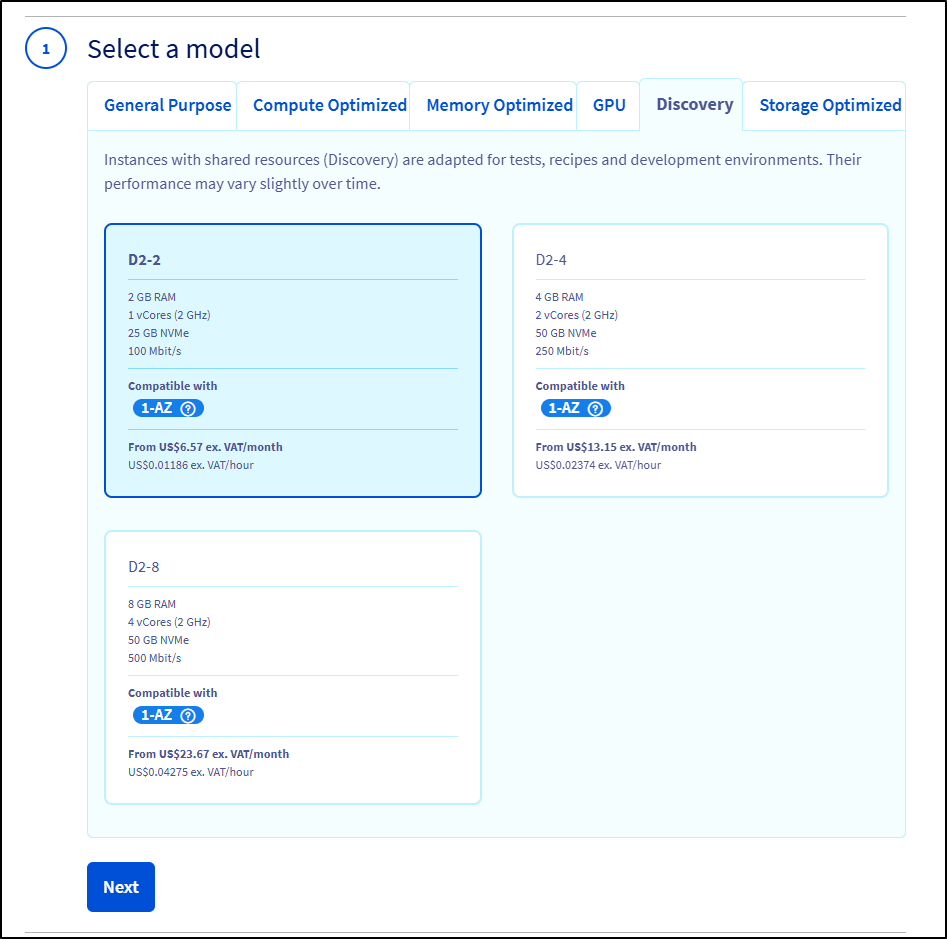
And I just ruled out OVHCloud as the smallest host I can get is a D2-2 and that would be US$8.65 a month
This makes for some interesting options. I could easily run a modded FTB minecraft server for $10/mo with a DNS name - and that’s if it ran 24/7.
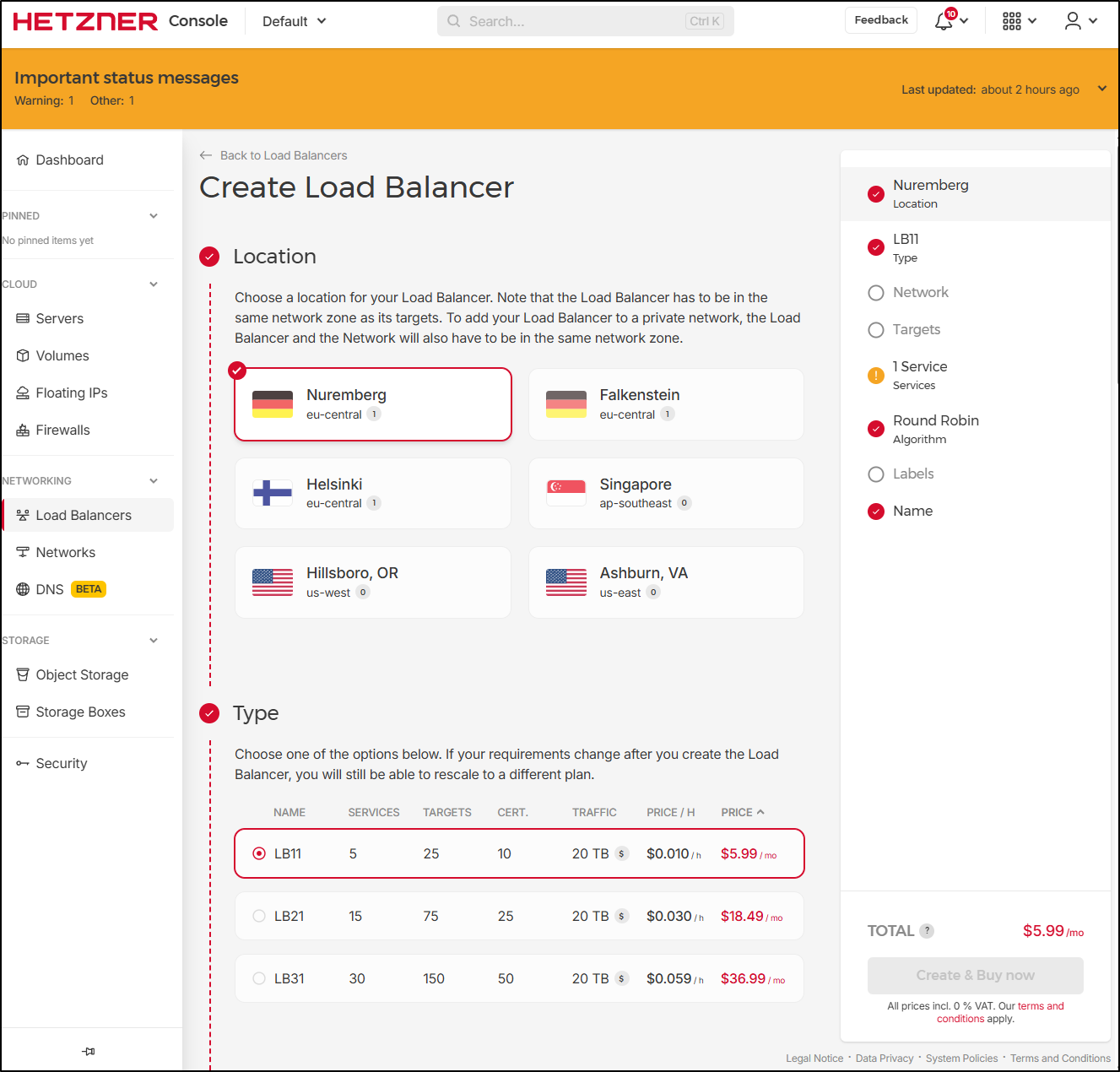
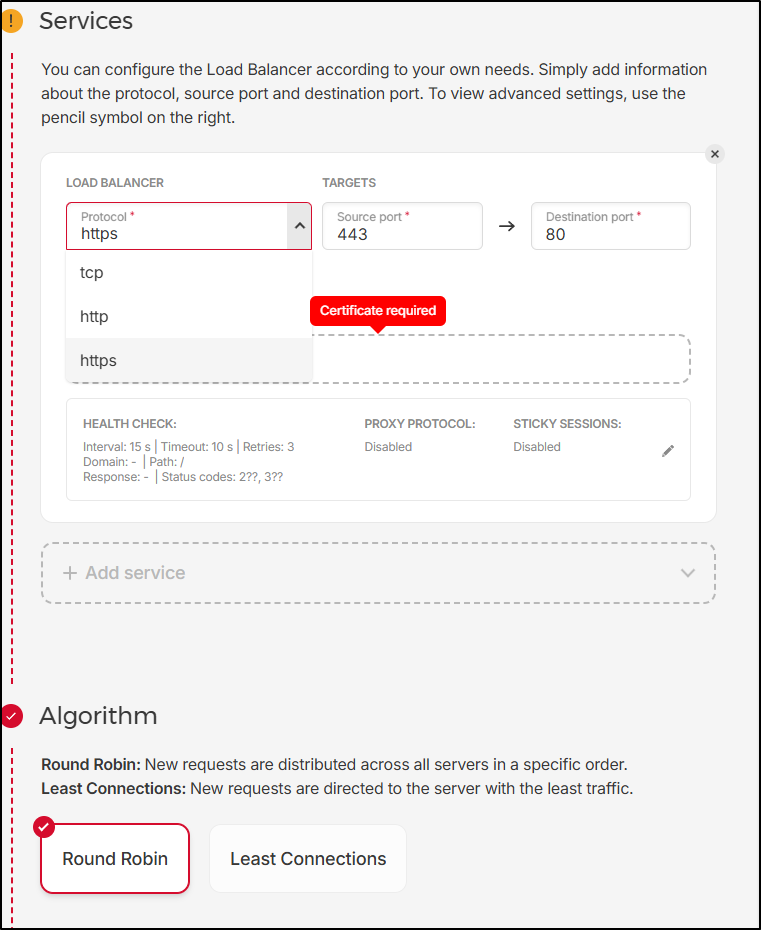
Load Balancers
We can create a basic LB for $6 a month under the Load Balancers section
We can easily do Layer 4 (tcp) or 7 (http)
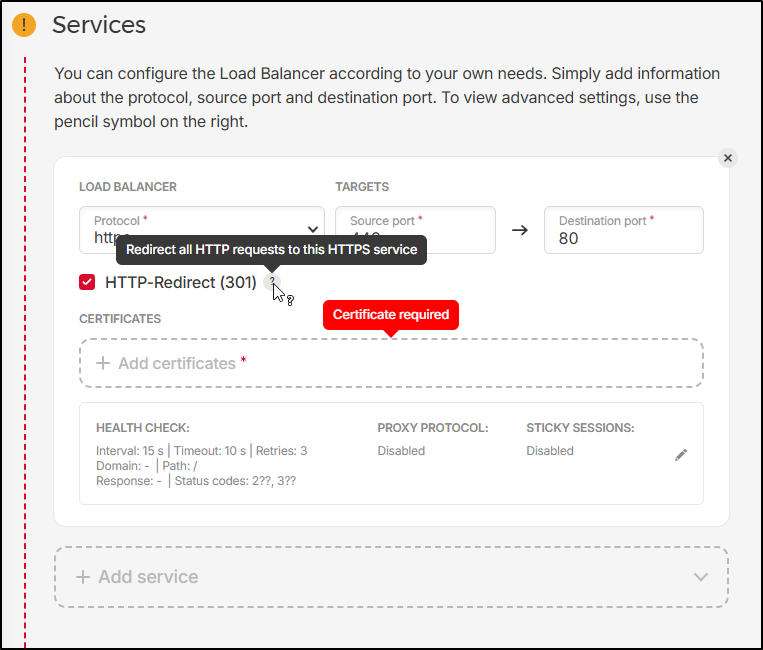
And handle things like HTTP redirects and sticky sessions (some old apps need that)
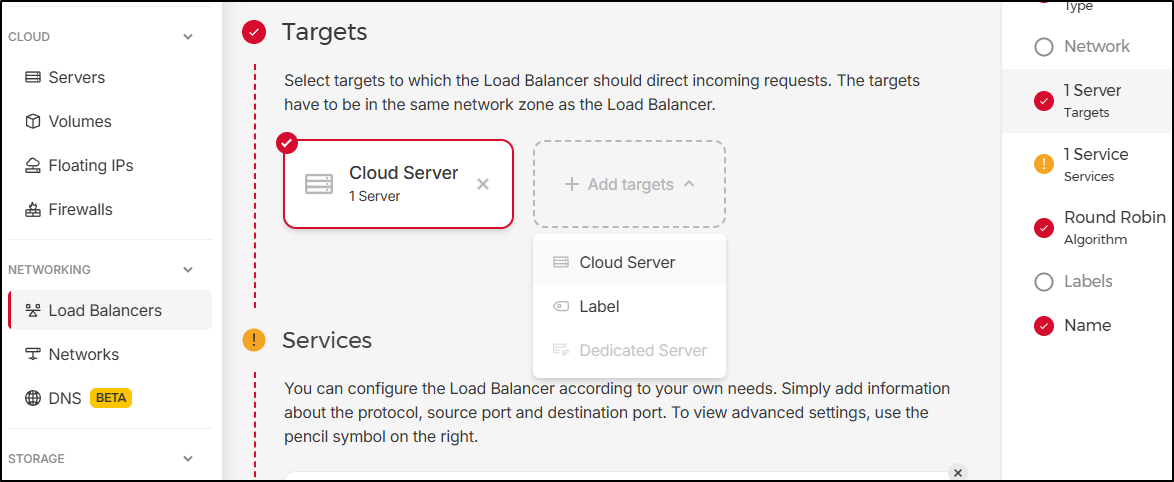
Sadly I won’t be able to use this LB to balance between UpCloud and Hetzner (at least directly) as I can really just pick from servers in Hetzner
Firewalls
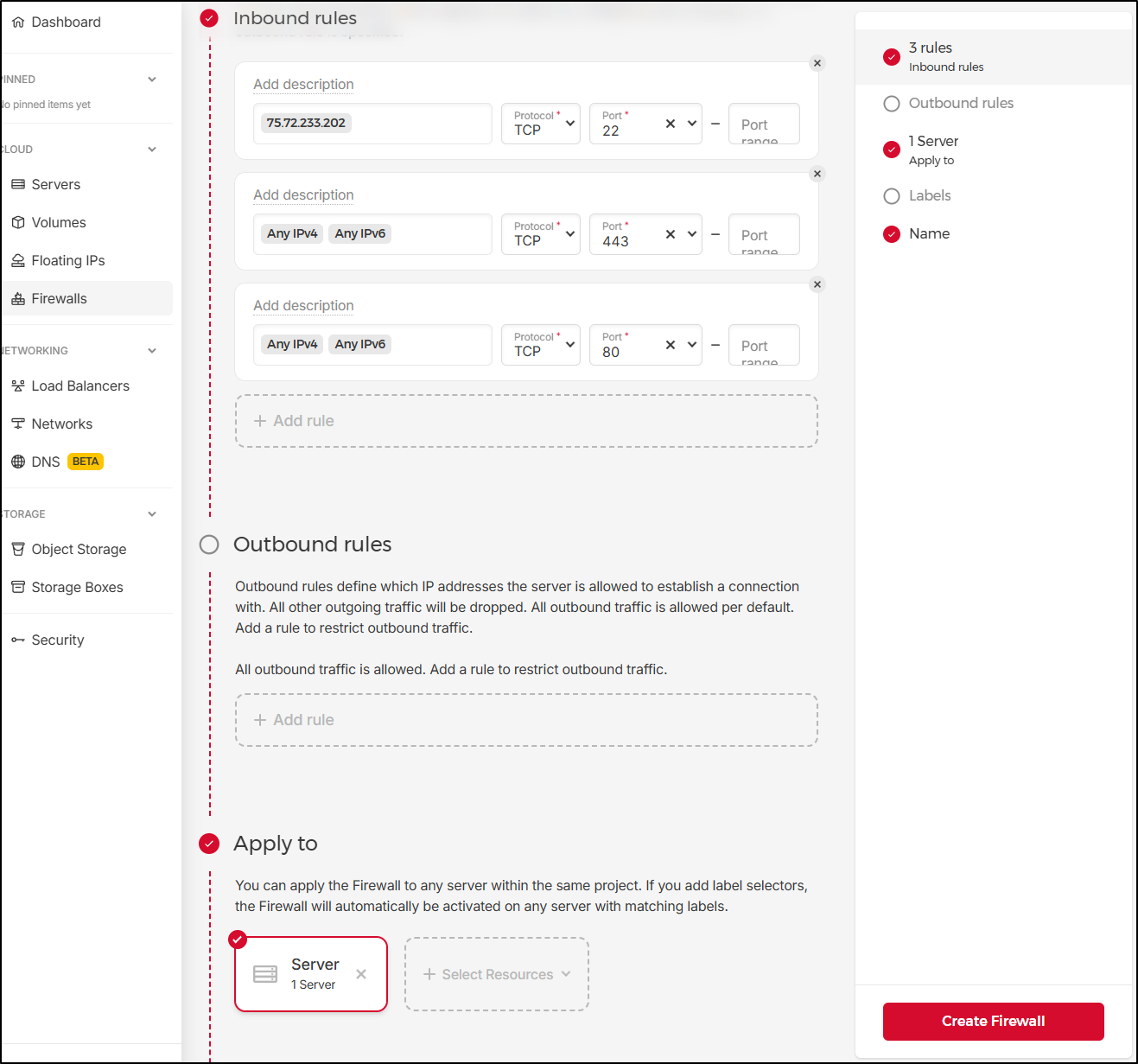
I prefer to handle the FW at the server level, but one can use the Cloud Firewall (free) to setup some rules to limit traffic
For instance, I could limit SSH to just my home address but HTTP/HTTPS from anywhere
With it applied, it will reduce the burden on the host and block traffic at the edge
But now I will not be able to SSH to this host from outside my network without modifying the Firewall first
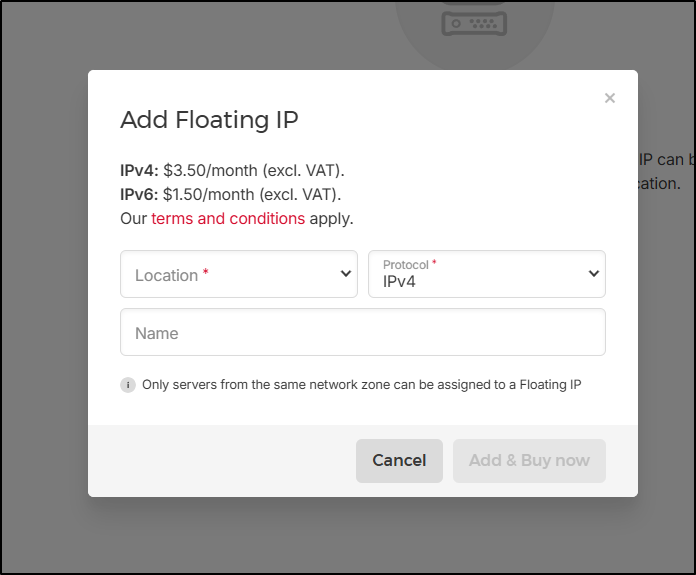
Floating IPs
In many ways, these are Loadbalancers in their simplest form. It’s just a public IP you rent and can point to whatever you want. It costs as must as a small server so I’m not sure the point
Summary
Today we looked at OVHCloud and Hetzner and compared them with what we just explored in UpCloud.
OVHCloud is fine, but spendy. I had to pay $1 just to create some projects and the price for hosting is higher than the rest. It does have more features in that there are Kubernetes instances and a whole AI/ML area I did not explore
Hetzner, while not as feature rich as UpCloud, has really good prices on hosts. The fact they give away DNS management is a real plus.
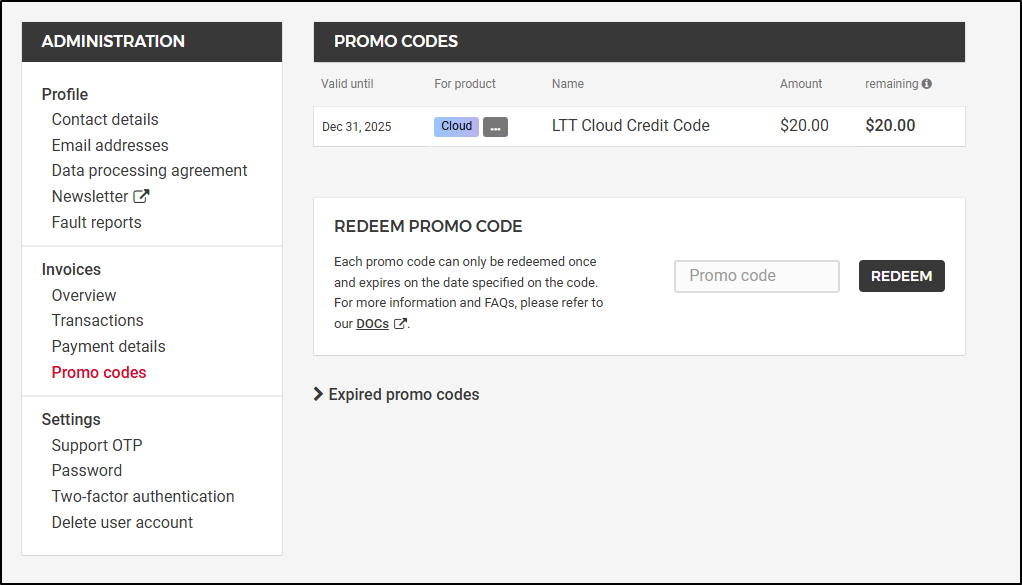
Hetzner also has promo codes. For instance, I found a Linus Tech Tips one (LTT25) worked to give me an extra $20:
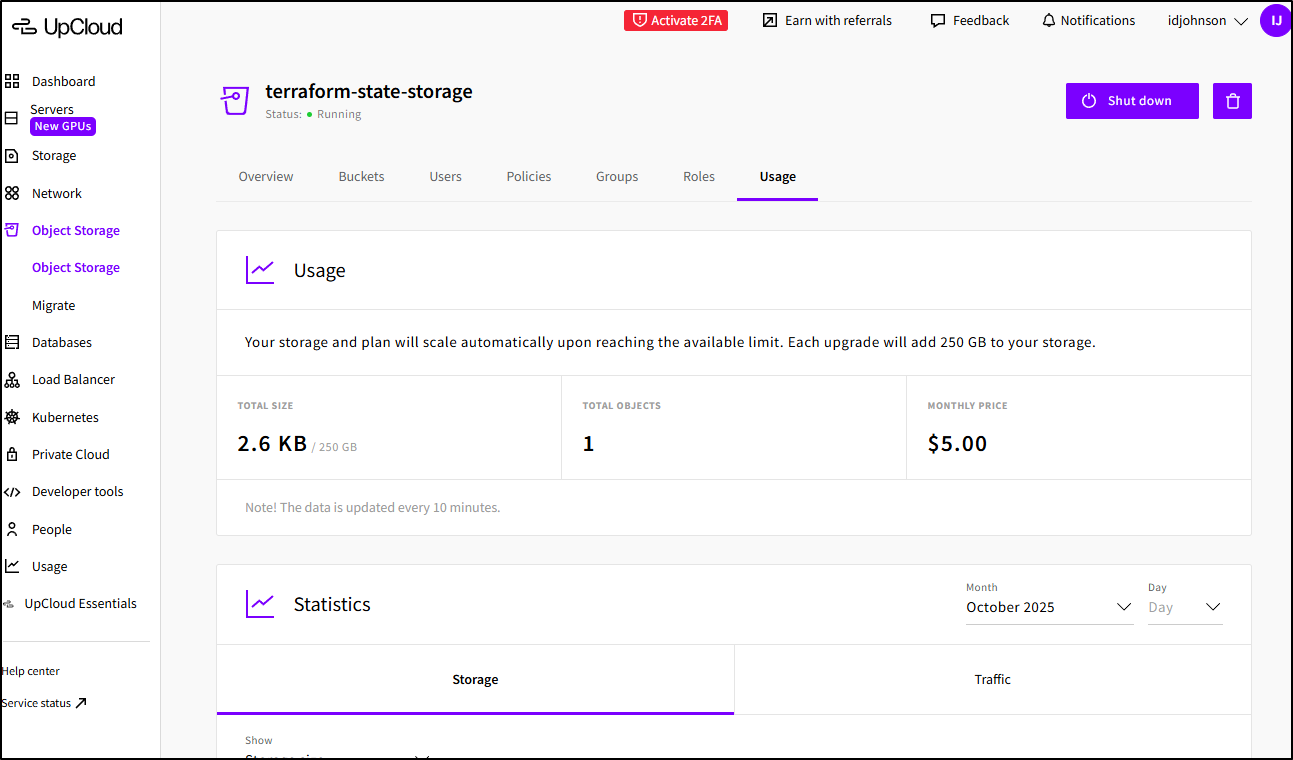
I like UpCloud - the developer tools are just excellent. But I am concerned it will add up. For instance, just stashing my 2.6Kb State file will run me $5 a month
I wanted to play so I did feed them some money - I’ll be using UpCloud for things - but likely in conjunction with Hetzner.
The other small issue I had is that OVHCloud only let me use US resources. The whole reason, imho, to use a non-US cloud provider is to get GTFO of the States. If I’m going to stay in the US, I might as well use GCP, Azure or AWS (or Akamai or DigitalOcean).